vpnpieces.com – Learn how VPN encryption works and discover its security benefits to protect your data and maintain privacy online. Understand the importance of VPNs.
What exactly is VPN encryption, and how does it help protect your online activities? Have you ever wondered why using a VPN is crucial for securing your data from hackers and ensuring privacy while browsing?
Let’s dive into the key security benefits of VPN encryption.
Table of Contents
ToggleWhat Is VPN Encryption and How Does It Work?
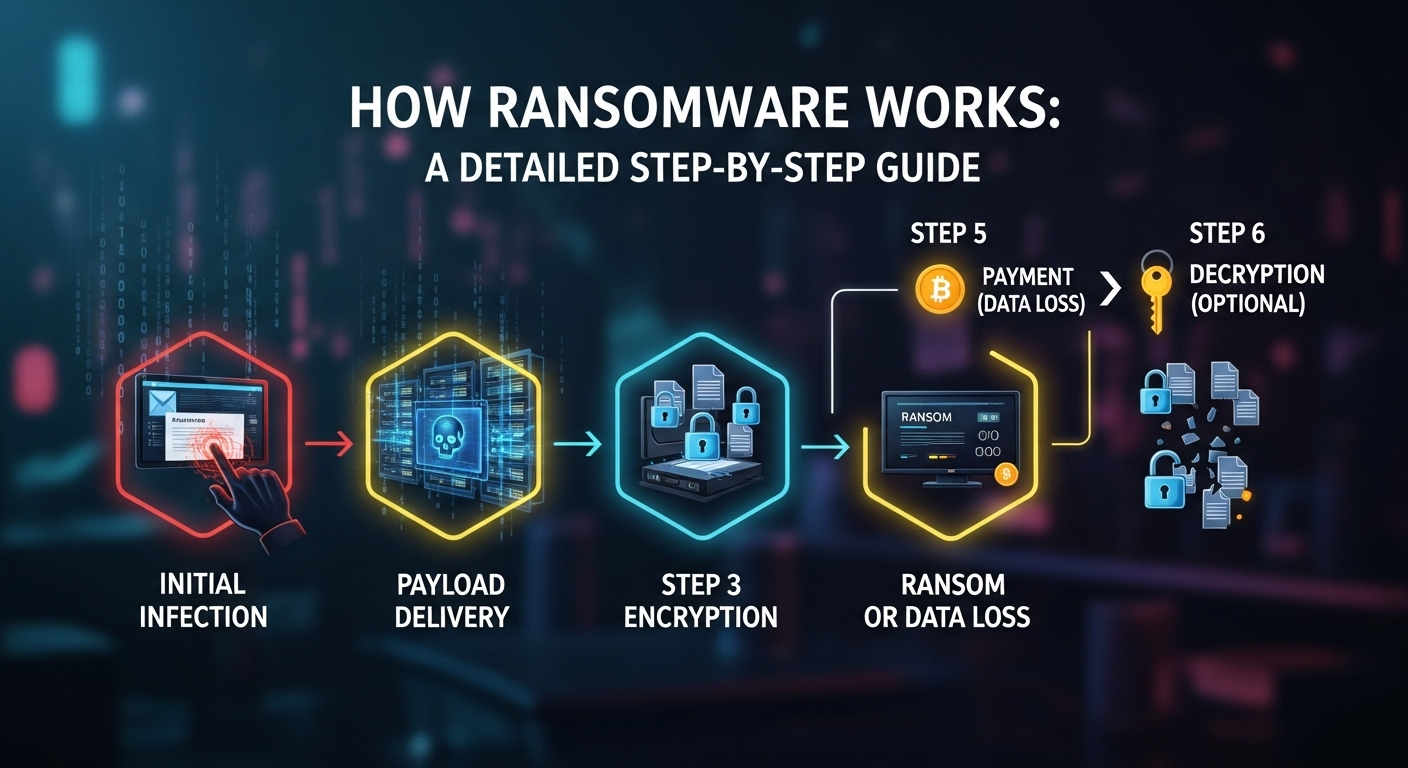
At its core, VPN encryption is the process of converting your internet traffic into an unreadable code as it travels between your device and the internet.
This is achieved using algorithms and secure protocols that form an encrypted VPN connection—making it nearly impossible for hackers, ISPs, or even governments to intercept and decipher your data.
When we connect to a secure VPN, our data is tunneled through a private server, which masks our real IP address and replaces it with one from the VPN provider.
This not only offers anonymous browsing protection but also establishes a secure tunneling protocol that forms the foundation of VPN security.
There are several types of encryption standards and protocols used in virtual private network security. The most common include AES encryption VPN (typically AES-256), IPsec VPN, and SSL VPN encryption. These standards ensure end-to-end encryption VPN services that maintain the confidentiality and integrity of your information during transmission.
Why VPN Encryption Matters More Than Ever

With cyber threats escalating globally, VPN encryption is not just a luxury—it’s a necessity. Data breaches, identity theft, and online tracking are rampant, and relying on unsecured connections is a high-risk game. A privacy-focused VPN empowers us to regain control over our digital lives.
One of the greatest strengths of data encryption VPN solutions lies in their ability to offer encrypted internet access even on unsecured networks.
Whether you’re accessing bank accounts or transferring sensitive business files, a VPN with military-grade encryption VPN capabilities ensures that your data is safe from prying eyes.
Additionally, the use of a private network encryption shields us from intrusive advertisers and data brokers who thrive on collecting user information. It provides us with the freedom to browse without leaving a digital footprint—ensuring true online privacy protection and peace of mind.
Key Components of a Secure VPN Setup
To fully leverage the benefits of VPN encryption, it’s important to understand the components that make up a robust virtual private network:
1. Encryption Protocols: These are the rules that define how data is encrypted and decrypted. IPsec, OpenVPN, WireGuard, and SSL are among the most secure tunneling protocols in use today.
2. VPN Ciphers: The algorithms used for encrypting data, like AES-256 or ChaCha20, are vital for security. AES encryption VPN standards are often referred to as “military-grade” due to their strength and reliability.
3. Kill Switches and DNS Leak Protection: A reliable VPN will automatically sever your internet connection if the encrypted tunnel drops. This ensures continuous protection and prevents any data from leaking through unencrypted channels.
By carefully selecting a VPN that incorporates these elements, we can ensure secure data transmission regardless of where or how we connect.
Benefits Beyond Privacy: The Broader Impact of Encrypted VPNs

While privacy is the most talked-about advantage, encrypted VPN connections offer several additional benefits that can improve our digital experiences:
– Bypassing Censorship and Geo-Restrictions: Secure VPNs allow access to global content by masking your location. This is particularly useful for accessing streaming platforms or news websites that may be restricted in certain regions.
– Protection on Public Wi-Fi: Airports, hotels, and cafés are hotspots for cyberattacks. A data encryption VPN ensures that your information remains safe even when connected to public networks.
– Enhanced Performance and Stability: Surprisingly, some VPNs can improve network performance by avoiding ISP throttling—where internet providers intentionally slow down your connection.
By using a privacy-focused VPN with encrypted internet access, we empower ourselves not only with security but also with digital freedom and efficiency.
Overcoming Common Challenges with VPN Encryption
Despite its advantages, VPN encryption isn’t without its hurdles. From speed concerns to legal and technical complexities, users often face obstacles that deter adoption.
1. Speed Reduction: Because your data is being routed through remote servers and encrypted, VPNs may slightly reduce connection speeds. However, choosing a high-quality, internet security VPN provider can minimize this impact with optimized infrastructure.
2. Compatibility Issues: Not all websites or applications play nicely with VPNs. Some streaming services, for example, actively block known VPN IP addresses. Using a VPN with a rotating IP or dedicated streaming servers can overcome this.
3. Legal Considerations: In some countries, using VPNs is restricted or monitored. It’s vital to check local laws and choose a provider that supports anonymous browsing protection and doesn’t keep logs.
With the right strategies and VPN provider, these challenges can be easily managed—ensuring a seamless and secure experience.
How to Choose the Right VPN for Encryption and Security
Selecting the right VPN for encrypted internet access requires careful consideration of several factors:
– Encryption Standards: Always opt for services offering AES encryption VPN or equivalent standards for maximum security.
– No-Log Policy: A truly private network encryption provider will not store your data or browsing history. This is critical for maintaining online privacy protection.
– Reputation and Transparency: Choose providers with a proven track record, transparent privacy policies, and positive reviews. Open-source platforms or those that have undergone independent audits are ideal.
– Cross-Platform Support: Look for VPNs that work seamlessly across desktop, mobile, and browser platforms—allowing you to maintain a secure VPN connection wherever you go.
By evaluating these criteria, we can make an informed choice that aligns with our security needs and personal browsing habits.
The Future of VPN Encryption in Cybersecurity
The demand for VPN encryption will only grow as digital threats become more sophisticated and pervasive. Innovations such as quantum-resistant cryptography, machine learning integration, and decentralized VPNs are paving the way for the next evolution in cybersecurity encryption.
Moreover, the shift toward hybrid work environments underscores the importance of reliable, secure VPN solutions for businesses. Organizations increasingly rely on encrypted data transmission to protect internal communications, customer data, and intellectual property.
As we continue to adopt emerging technologies, staying informed about advancements in VPN cipher methods and secure tunneling protocols will be essential. VPN encryption is no longer a tool reserved for tech-savvy users—it’s becoming a foundational element of modern internet safety.