In an age where our lives are increasingly intertwined with the digital world, the concepts of online privacy and security have shifted from niche concerns to mainstream necessities. Every click, search, and transaction sends data packets flying across the public internet, a space akin to a bustling public square where conversations can be overheard. This is where a Virtual Private Network, or VPN, becomes an indispensable tool. But have you ever stopped to wonder about the intricate digital dance that happens in the seconds after you click "Connect"? Understanding how a VPN connection is established is the key to appreciating the powerful protection it provides. This guide will demystify the process, breaking down the complex steps of authentication, tunneling, and encryption into a simple, step-by-step journey.
Table of Contents
ToggleThe Foundations: What is a VPN and Why Do You Need One?
At its core, a Virtual Private Network (VPN) is a service that creates a secure and encrypted connection over a less secure network, such as the public internet. The best way to visualize this is to imagine the internet as a vast, open highway system. Without a VPN, your data travels on this highway in a clear glass car, allowing your Internet Service Provider (ISP), network administrators, and potential bad actors to see where you're going and what you're carrying. A VPN, however, builds a private, opaque tunnel for your car. Inside this tunnel, your vehicle is invisible, and its contents are locked in an unbreakable safe.
The primary purpose of a VPN is to enhance your privacy, security, and anonymity online. Security is achieved through robust encryption, which scrambles your data, making it completely unreadable to anyone who might intercept it. This is particularly crucial when using public Wi-Fi networks in places like cafes, airports, or hotels, which are notorious hotspots for cybercriminals looking to steal sensitive information like passwords and credit card details. Privacy is preserved by masking your true IP address—your unique identifier on the internet—and replacing it with the IP address of the VPN server. This prevents websites, advertisers, and even your ISP from tracking your online activities and building a profile based on your browsing habits.
The practical applications of this technology are vast and varied. For remote workers, a VPN is essential for securely accessing a company's internal network and sensitive files from home or while traveling, ensuring that confidential business data remains protected. For the everyday user, it's a powerful tool for bypassing geo-restrictions, allowing you to access content and services that might be unavailable in your region. By connecting to a server in a different country, you can effectively "teleport" your digital location, unlocking international streaming libraries or accessing websites that are blocked locally. Ultimately, a VPN gives you greater control over your digital footprint and restores a measure of freedom and privacy to your online experience.
The First Handshake: Authentication and Authorization
The very first step in establishing a VPN connection is a digital "handshake" known as authentication and authorization. This process is all about verification. Before a secure tunnel can be built, the VPN server needs to confirm two critical things: first, that you are who you say you are (authentication), and second, that you have the right to use the service (authorization). This initial phase is initiated the moment you open your VPN application and click the "Connect" button. Your device's VPN client immediately sends a connection request to the VPN server you've selected.
Authentication is the process of proving your identity. In most cases, this is handled through a username and password that you created when you signed up for the VPN service. When your VPN client contacts the server, it presents these credentials. The server then cross-references this information with its database of registered users. This is analogous to a security guard checking your photo ID against a guest list before letting you into an exclusive event. Some more advanced systems might use digital certificates or multi-factor authentication (MFA) for an even higher level of security, requiring a second form of verification, such as a code sent to your phone.
Once your identity has been successfully authenticated, the server moves on to authorization. This step confirms that your account is in good standing and has permission to establish a connection. The server checks details like whether your subscription is active and paid for, or if your account has been flagged for any violations of the terms of service. If both authentication and authorization are successful, the server gives the green light to proceed to the next stage: building the secure tunnel. If either step fails, the connection is immediately terminated, and your VPN client will typically display an error message.
- #### The Role of Your VPN Client
The VPN client is the software application you install on your computer, smartphone, or another device. It serves as the command center for your VPN connection, acting as the crucial intermediary between you and the VPN server. This software is responsible for storing your login credentials securely and presenting them to the server during the authentication phase. It also houses the necessary configurations and protocols required to initiate and maintain a stable connection.
When you select a server location and hit "Connect," it's the client's job to package this request and send it out over the internet. This isn't just a simple message; it's a carefully structured communication packet that tells the server your identity and your intent to build a secure tunnel. The client handles the complexities of this initial negotiation, ensuring that it speaks the same "language" as the server to facilitate a smooth and successful handshake.
- #### Server-Side Verification
On the other end of the initial request is the VPN server, a powerful computer located somewhere in the world, waiting for connection requests from clients. When your request arrives, the server’s software immediately begins its verification process. It unpacks the data packet sent by your client and extracts the authentication credentials.
The server's primary task here is to be a vigilant gatekeeper. It rigorously checks the provided username and password (or other credentials) against its secure user database. This is a critical security checkpoint. If the credentials match and the account is authorized for access, the server sends back an affirmative response to your client, signaling that the handshake was successful and the next stage can begin. If there's any discrepancy, the server rejects the connection, protecting its network from unauthorized access.
Building the Tunnel: The Role of Tunneling Protocols
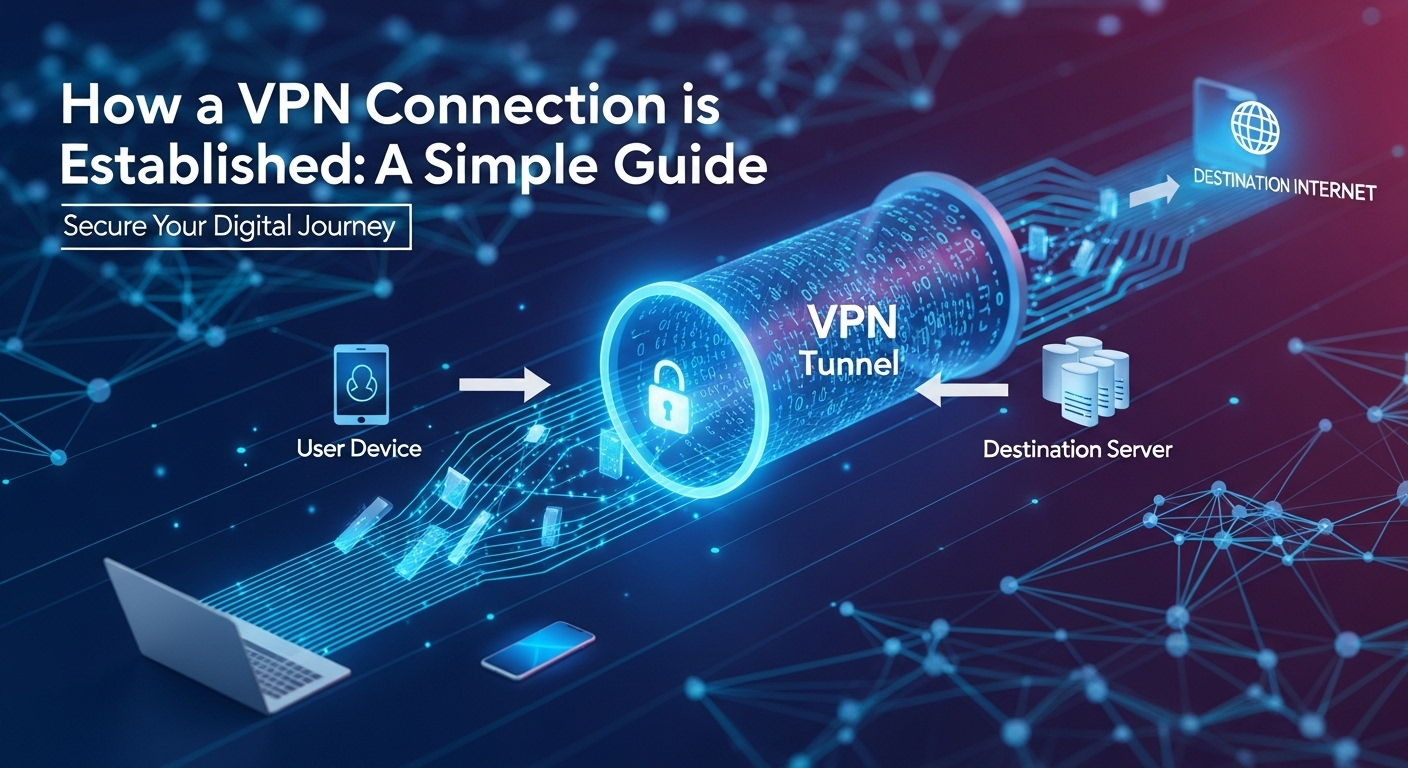
With authentication and authorization complete, the next phase is to construct the "Virtual Private Network" itself. This is achieved through a process called tunneling. In essence, tunneling involves taking your internet data packets and wrapping them inside other data packets before sending them across the public network. This outer packet acts as a protective shell, hiding the contents and true destination of your original data. The pathway created by this process is the "tunnel" that connects your device directly to the VPN server, shielding your traffic from your ISP and anyone else on the local network.
To build and manage this tunnel, VPNs rely on a set of rules and procedures known as tunneling protocols. A protocol is like a blueprint that defines exactly how the tunnel should be structured, how data should be encapsulated, and how to ensure the connection remains stable. There is no single "best" protocol; instead, different protocols offer varying balances of speed, security, and reliability. The choice of protocol can significantly impact your VPN experience, which is why many VPN providers allow users to switch between them.
The most common protocols include OpenVPN, a highly configurable and secure open-source veteran; IKEv2/IPsec, known for its stability and speed, especially on mobile devices; and WireGuard, a modern, lightweight protocol that offers exceptional speeds and state-of-the-art cryptography. When your VPN client and server agree to connect, they also agree on which protocol to use. This agreement ensures that both ends of the connection are following the same set of rules to create a seamless and secure data tunnel.
- #### Comparing Popular VPN Protocols
Choosing the right VPN protocol can feel technical, but understanding the key differences can help you optimize your connection for your specific needs. Each protocol was designed with different priorities in mind, leading to a trade-off between performance and security features. For example, a protocol built for maximum security might have a slightly higher overhead, leading to a small reduction in speed, while one built for speed might use more modern, leaner code.
The table below provides a high-level comparison of the three most popular protocols used by commercial VPN services today. This can help you decide whether you need the rock-solid security of OpenVPN for handling sensitive data, the mobile-friendly stability of IKEv2, or the blazing-fast speeds of WireGuard for streaming and gaming.
| Protocol | Speed | Security | Stability | Common Use Case |
|---|---|---|---|---|
| OpenVPN | Good | Excellent | Excellent | The all-around standard for desktop users who prioritize security and configurability. |
| IKEv2/IPsec | Very Good | Very Good | Excellent | Ideal for mobile users as it can quickly re-establish a connection when switching networks (e.g., from Wi-Fi to cellular). |
| WireGuard | Excellent | Excellent | Very Good | Perfect for tasks that demand high speed, such as 4K streaming, online gaming, and large file downloads. |
- #### What is Encapsulation?
Encapsulation is the core technical process behind tunneling. To understand it, think of sending a postcard. A postcard is open for anyone to read. Encapsulation is the act of taking that postcard (your data packet), putting it into a sealed, private envelope (the new packet), and writing a new address on the outside (the VPN server’s IP address).
In networking terms, your original data packet, which contains information like its final destination (e.g., youtube.com) and your source IP address, is taken and wrapped inside a new, outer packet created by the VPN protocol. This process effectively hides the original packet's header information. Now, anyone monitoring your traffic, like your ISP, can only see the outer packet. They can see that you are sending data to a VPN server, but they have no idea what that data is or where it's ultimately headed. This is the foundational mechanism that makes a VPN a "private" network.
Securing the Data: The Encryption Process
Simply building a tunnel isn't enough to guarantee security. While tunneling hides your data's destination, the data itself could still be vulnerable if the tunnel were ever breached. This is where encryption comes in. Encryption is the process of using a sophisticated algorithm to scramble your data into an unreadable format known as ciphertext. It is the lock on the unbreakable safe inside your private tunnel. Without the correct "key," this scrambled data is nothing more than a meaningless jumble of characters to anyone who intercepts it.
The strength of this encryption is paramount to your security. The current industry gold standard is AES (Advanced Encryption Standard) with 256-bit keys. This is a symmetric encryption cipher, meaning the same key is used to both encrypt and decrypt the data. The "256-bit" refers to the length of the key, and a longer key means an exponentially higher number of possible combinations. To put it into perspective, trying to brute-force a 256-bit key would take the world's most powerful supercomputers billions of years, making it effectively unbreakable.
This encryption process happens in real-time. As data leaves your device, the VPN client encrypts it before sending it into the tunnel. When the data arrives at the VPN server, the server uses the shared key to decrypt it before forwarding it to the public internet. The same process happens in reverse for incoming data. This constant encryption and decryption ensures that your information remains completely confidential and secure throughout its entire journey between your device and the VPN server.
- #### Symmetric vs. Asymmetric Encryption
To understand how the encryption key is securely shared, it’s important to know the two main types of encryption. Symmetric encryption, as used by AES, is extremely fast and efficient. It uses a single, shared secret key to both encrypt and decrypt data. This is perfect for the ongoing data transfer in a VPN session, as it doesn’t add much processing overhead, keeping your connection speedy. The only challenge is: how do the client and server agree on this secret key at the beginning of the session without an eavesdropper seeing it?
This is where asymmetric encryption (also known as public-key cryptography) comes in. This method uses a pair of keys: a public key, which can be shared with anyone, and a private key, which is kept secret. Data encrypted with the public key can only be decrypted by the corresponding private key. This system is slightly slower than symmetric encryption but is perfect for securely exchanging information, like a secret key.
- #### The Encryption Handshake Explained
At the start of the VPN connection, right after authentication, the client and server perform an “encryption handshake” to securely establish a shared key for the session. This process typically uses asymmetric encryption. The server sends its public key to your VPN client. Your client then generates a new, random symmetric key (the one that will be used for the AES encryption) for this specific session. It encrypts this new session key using the server’s public key and sends it back.
Because the session key was encrypted with the server's public key, it can only be decrypted by the server's private key. This means that even if a hacker intercepted this exchange, they wouldn't be able to decipher the session key. Once the server decrypts the message with its private key, both the client and the server now possess the same secret symmetric key. They can then switch to the much faster AES symmetric encryption for the remainder of the session, confident that their communication line is secure.
The Final Step: Routing Your Traffic
Once the authenticated, encrypted tunnel has been successfully established, the final stage of the process begins: routing your internet traffic. At this point, your VPN connection is fully active. The VPN client on your device reconfigures your device's networking settings to ensure that all outgoing internet traffic—from your web browser, email client, gaming application, and more—is now sent through this secure tunnel first, rather than directly to your ISP.
Your data, now fully encrypted, travels through the tunnel to the VPN server you selected. Upon arrival, the server performs a critical function. It decrypts your data packets, reads the original destination address (e.g., google.com or netflix.com), and then forwards your request to that final destination on the public internet. Crucially, when the server sends this request, it uses its own IP address, not yours. To the destination website, it appears as if the request originated directly from the VPN server.
This re-routing process is the magic behind how a VPN masks your IP address and spoofs your location. The website you're visiting has no knowledge of your true IP address or physical location; it only communicates with the VPN server. This provides a powerful layer of anonymity and is the mechanism that allows you to bypass geographic firewalls and censorship. All the website sees is a request from a server in London, Tokyo, or New York, depending on which one you chose to connect to.
- #### The Return Trip: How Data Comes Back to You
The process doesn’t end with your request being sent out. When the destination website (e.g., a news site) sends a response, it sends it back to the address that requested it—the VPN server’s IP address. The VPN server receives this incoming data, which could be the contents of a webpage, a streaming video file, or an email.
Before sending it back to you, the server performs the security process in reverse. It encrypts the incoming data using the shared session key (the AES-256 key established during the handshake) and sends it back to your device through the secure tunnel. Your VPN client receives these encrypted packets, uses its identical session key to decrypt them instantly, and then passes the data along to the appropriate application on your device, allowing you to view the webpage or watch the video. This entire round-trip happens in milliseconds but ensures end-to-end encryption for both your outgoing and incoming traffic.
- #### Understanding IP Masking and Geolocation
The concept of IP masking is fundamental to VPN privacy. Your real IP address can reveal a surprising amount of information about you, including your approximate geographical location (city or region), your ISP, and your browsing activity. By routing your traffic through a VPN server, you effectively swap your IP address for the server’s IP address. This “mask” prevents websites and online trackers from identifying you and following you across the web.
This same mechanism is what unlocks geo-restricted content. Streaming services like Netflix and Hulu use your IP address to determine your location and show you the content library licensed for that region. By connecting to a VPN server in the United States, your traffic appears to originate from the US, granting you access to the American content library. This ability to change your virtual location not only provides entertainment benefits but also serves as a critical tool for journalists, activists, and citizens in countries with heavy internet censorship, allowing them to access a free and open internet.
Frequently Asked Questions (FAQ)
Q: Does a VPN make me completely anonymous?
A: A VPN provides a very high level of privacy but not absolute anonymity. It hides your IP address and encrypts your traffic from your ISP and other third parties. However, your VPN provider can still potentially see your activity. This is why it is critically important to choose a reputable VPN with a strict and audited no-logs policy. True anonymity is a complex state that often requires additional tools like the Tor network.
Q: Will a VPN slow down my internet connection?
A: A VPN will almost always introduce some reduction in speed. This is due to two factors: the processing power required for encryption and decryption, and the physical distance the data must travel to the VPN server and back. However, with premium VPN services and modern protocols like WireGuard, the speed loss is often negligible and may not be noticeable for everyday browsing and streaming. Connecting to a server that is geographically closer to you can help minimize latency.
Q: Is using a VPN legal?
A: In the vast majority of countries, including the United States, Canada, and most of Europe, using a VPN is perfectly legal. VPNs are legitimate tools used by millions of individuals and corporations for privacy and security. However, using a VPN to conduct illegal activities is still illegal. A small number of countries with authoritarian regimes have banned or restricted VPN use, so it's wise to check the local laws if you are traveling.
Q: What's the difference between a VPN and a proxy?
A: The main difference is the scope and level of security. A proxy server typically only re-routes the traffic for a specific application, like your web browser, and often does not provide strong encryption. A VPN, on the other hand, operates at the operating system level, creating an encrypted tunnel for all of your device's internet traffic. This makes a VPN a far more comprehensive and secure solution for overall online privacy.
Conclusion
The process of establishing a VPN connection is a sophisticated symphony of cryptographic and networking technologies working in perfect harmony. It all begins with a secure authentication to verify your identity, followed by the creation of a private tunnel using a specific protocol. Within this tunnel, all your data is scrambled with powerful encryption, rendering it unreadable to outsiders. Finally, your traffic is routed through the VPN server, which masks your real IP address and sends your requests to the internet on your behalf.
From the initial digital handshake to the final routing of your data, every step is designed with one goal in mind: to reclaim your privacy and secure your data in an increasingly transparent digital world. Understanding how a VPN connection is established not only demystifies the technology but also deepens our appreciation for the essential shield it provides against the prying eyes of ISPs, advertisers, and malicious actors. In today's connected era, a VPN is no longer a luxury for the tech-savvy; it is a fundamental tool for digital citizenship.
***
Article Summary
This article provides a simple, in-depth guide to how a VPN connection is established. It covers the entire process from start to finish, explaining complex concepts with easy-to-understand analogies.
- Foundations: A VPN (Virtual Private Network) creates a secure, encrypted tunnel over the public internet to provide privacy, security, and anonymity. It's used to protect data on public Wi-Fi, bypass geo-restrictions, and enable secure remote work.
- Authentication & Authorization: The first step is a "handshake" where the VPN client proves your identity (authentication) to the VPN server, which then confirms you have permission to use the service (authorization).
Tunneling: After authentication, a "tunnel" is created using a tunneling protocol (OpenVPN,IKEv2,WireGuard*). This involves encapsulating your data packets inside new packets, hiding their original content and destination from your ISP.
- Encryption: Inside the tunnel, all data is scrambled using strong encryption like AES-256. The process begins with an "encryption handshake" using asymmetric encryption to securely share a symmetric key that is used for the rest of the session.
- Routing: Finally, your encrypted traffic is sent through the tunnel to the VPN server. The server decrypts it, sends it to the intended website using its own IP address (masking yours), and then encrypts the response before sending it back to you.
- FAQ: The article concludes with an FAQ section addressing common questions about VPN anonymity, speed, legality, and the difference between a VPN and a proxy.
















