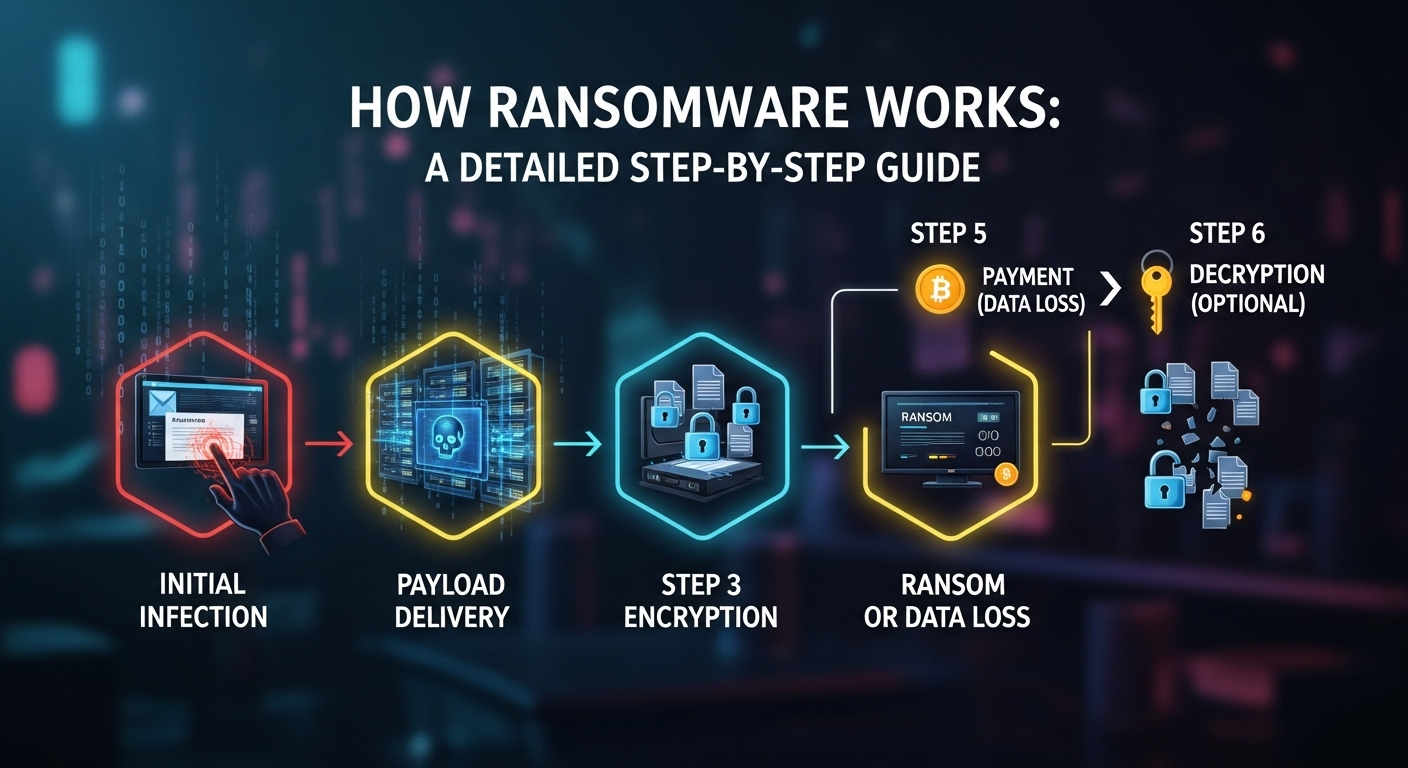
In an age where our lives are inextricably linked to digital data, the threat of losing access to it all is more terrifying than ever. Imagine one day turning on your computer only to find every single file—family photos, critical work documents, financial records—locked away by a digital padlock, with a menacing note demanding a hefty sum for the key. This is not a scene from a sci-fi movie; it is the reality of a ransomware attack. Understanding the mechanics behind this pervasive cyber threat is the first and most crucial step in defending against it. This guide will provide a detailed, step-by-step breakdown of how does ransomware work, from the initial breach to the final, tense moments of extortion.
Table of Contents
ToggleThe Initial Breach: Gaining Access to the System
Every ransomware attack begins with a single, critical moment: the breach. Threat actors, the individuals or groups behind these attacks, employ a variety of sophisticated and sometimes surprisingly simple techniques to infiltrate a target's network or device. This initial access is the foundation upon which the entire attack is built. Without it, the ransomware payload can never be deployed, and the subsequent chaos can be avoided. The methods used are constantly evolving, but they generally fall into a few key categories that exploit both technological vulnerabilities and human psychology.
The goal of this initial phase is not to encrypt files immediately but to establish a foothold. Think of it as a burglar successfully picking the lock on a front door. They are inside the house, but they haven't started taking valuables yet. They will first scout the area, disable alarms, and ensure they can operate without being detected. Similarly, after a successful breach, the malicious software will often lie dormant or perform quiet reconnaissance, preparing the environment for the main event. This stealthy approach makes early detection incredibly difficult without advanced security monitoring tools.
Understanding these entry points is paramount for building an effective defense. By shoring up the most common infiltration vectors, organizations and individuals can significantly reduce their attack surface and decrease the likelihood of becoming a victim. It’s a constant cat-and-mouse game where defenders must patch vulnerabilities and train users, while attackers relentlessly search for the next weak link.
Phishing and Social Engineering: The Human Element
The single most common delivery method for ransomware remains phishing. This social engineering technique preys on human trust and curiosity. Attackers craft deceptive emails that appear to be from a legitimate source—a bank, a colleague, a delivery service, or even an internal IT department. These emails often create a sense of urgency or fear, prompting the recipient to click a malicious link or download a compromised attachment without thinking twice. A classic example is an email with a subject like "Urgent: Invoice Overdue" containing an attached Word document or PDF.
Once the recipient opens the attachment, they might be prompted to "Enable Content" or "Enable Macros" to view the document properly. This action is the trigger that executes a hidden script, downloading the ransomware payload from a remote server onto the victim's computer. Similarly, clicking a malicious link can redirect the user to a spoofed login page designed to steal credentials or to a website that uses an exploit kit to silently install the malware. Spear phishing is an even more targeted and dangerous variant, where attackers research their victim and craft a highly personalized email that is much harder to recognize as fraudulent.
Exploit Kits and Unpatched Vulnerabilities
While phishing relies on human error, other methods exploit purely technical weaknesses. Attackers are constantly scanning the internet for systems running outdated software with known vulnerabilities. This includes unpatched operating systems (like Windows or macOS), web browsers, and third-party plugins such as Adobe Flash Player or Java. When a security flaw is discovered, software vendors release a patch to fix it. However, many users and organizations fail to apply these patches promptly, leaving a window of opportunity for attackers.
An exploit kit is a toolkit hosted on a compromised website that automates the process of exploiting these vulnerabilities. When a user with an unpatched system visits such a site (often redirected there via a malicious ad, or malvertising), the exploit kit scans their browser and plugins for any known weaknesses. If one is found, the kit automatically deploys an exploit to gain control of the system and deliver the ransomware payload. This entire process happens silently in the background, without any further action required from the user, making it an incredibly effective infiltration method.
Remote Desktop Protocol (RDP) and Weak Credentials
Remote Desktop Protocol (RDP) is a feature built into Windows that allows users to connect to and control another computer over a network. It is an invaluable tool for system administrators and remote workers. However, when poorly secured, it becomes a wide-open door for attackers. Cybercriminals scan the internet for computers with open RDP ports (typically port 3389) and then attempt to gain access using a variety of methods.
The most common approach is a brute-force attack, where automated software tries thousands of common username and password combinations until it finds one that works. This is particularly effective against accounts with weak, easily guessable passwords like "123456" or "password." Alternatively, attackers can purchase stolen RDP credentials from dark web marketplaces. Once they have legitimate access, they can log in just like an authorized user, disable security software, and manually deploy the ransomware across the entire network.
The Infection and Establishment Phase
Once the initial breach is successful, the ransomware doesn't just start encrypting files immediately. Doing so would be rash and could lead to early detection and removal. Instead, the malware enters a crucial second phase: establishing itself on the system, escalating its privileges, and preparing the battlefield for the main attack. This stage is characterized by stealth and sabotage, as the ransomware works to solidify its control and dismantle any potential defenses that could interfere with its ultimate goal.
During this phase, the malware aims to become a persistent part of the system. It needs to ensure that it can survive a simple reboot and continue its operations. It also actively seeks to gain higher levels of access, moving from a standard user account to an administrative or system-level account. With these elevated privileges, the ransomware can execute more powerful commands, including the critical and destructive step of disabling security software and deleting system backups, effectively trapping the victim.
Payload Execution and Privilege Escalation
The initial entry vector—whether a phishing email attachment or an exploit kit—often delivers a small, lightweight piece of malware known as a dropper or loader. The dropper's sole purpose is to connect to a command-and-control (C&C) server controlled by the attacker and download the main ransomware payload. This two-stage approach helps evade initial detection, as the dropper itself may not appear malicious to basic antivirus scanners.
After the full ransomware payload is on the system, its next objective is privilege escalation. Most users operate on standard accounts with limited permissions, which prevents them from making system-wide changes. The ransomware needs to overcome this. It will use various techniques to exploit vulnerabilities within the operating system to gain administrative rights. Once it has these elevated privileges, it has the keys to the kingdom. It can now modify system files, stop critical services, and access data belonging to all users on the machine.
Establishing Persistence and Disabling Defenses
To ensure its long-term survival, the ransomware must establish persistence. This means it modifies the system so that it automatically runs every time the computer is started. Common methods include adding entries to the Windows Registry's "Run" keys, creating a new service, or placing a file in the system's startup folder. By achieving persistence, the ransomware guarantees that even if the victim reboots their computer in an attempt to stop the encryption process, the attack will simply resume.
With persistence and administrative rights secured, the ransomware begins its most cynical task: systematically dismantling the victim's defenses. It will attempt to terminate the processes of antivirus and anti-malware software, effectively blinding the system's digital immune system. Even more devastatingly, it will specifically target and delete any available backups. This includes using built-in Windows commands like `vssadmin` to delete Volume Shadow Copies—local snapshots of files that could otherwise be used for recovery. By destroying backups, the attackers dramatically increase the pressure on the victim to pay the ransom, as it eliminates the most viable alternative for data restoration.
The Encryption Process: The Heart of the Attack
This is the phase where the ransomware lives up to its name. After gaining access, escalating privileges, and disabling defenses, the malware unleashes its primary weapon: encryption. This process is the core of the attack, transforming the victim's valuable data into an unreadable, scrambled mess. The
encryption itself is not a crude lock; modern ransomware employs powerful, military-grade cryptographic algorithms that are, for all practical purposes, impossible to break without the unique decryption key.
The ransomware works methodically, but quickly. It's a race against time to encrypt as many valuable files as possible before the user notices and shuts down the system. The malware is programmed to be efficient, targeting specific file types and locations while carefully avoiding critical system files that are necessary for the computer to remain operational. After all, the attacker needs the victim to be able to turn on their computer to see the ransom note and make the payment.
Scanning for and Identifying Target Files
The encryption process begins with a rapid scan of all accessible drives, including local hard drives, attached external drives, and mapped network shares. This is why a single infected computer can lead to the encryption of an entire organization's shared files. The ransomware is programmed with a long list of file extensions to look for. It's not interested in locking system files like DLLs or EXEs, as this would crash the computer.
Instead, its targets are the files that hold the most value for the user or business:
- Documents: .doc, .docx, .xls, .xlsx, .ppt, .pdf
- Images and Videos: .jpg, .png, .gif, .mp4, .mov
- Databases: .sql, .mdb, .db
- Archives: .zip, .rar
- Project Files: .psd, .cad, .dwg
As it finds these files, it begins the encryption process, often replacing the original file with its encrypted version and appending a new, unique extension (e.g., `document.docx` becomes `document.docx.locked`). This systematic targeting ensures maximum damage to the victim's productivity and personal data.
The Encryption Algorithm: Locking Your Data
Modern ransomware uses a hybrid encryption model that combines the speed of symmetric encryption with the security of asymmetric (public-key) encryption. Here’s a simplified breakdown:
- For each file, the ransomware generates a new, unique symmetric key (e.g., using a strong algorithm like AES-256). It uses this single key to quickly encrypt the contents of that file.
- Now, the ransomware needs to protect this symmetric key. It does so using a public key (e.g., using an algorithm like RSA-2048) that was embedded in the ransomware or downloaded from the attacker's server. This public key is part of a key pair.
- The symmetric key is encrypted with the attacker's public key. This newly encrypted symmetric key is then stored, often within the encrypted file's header or at the end of the file.
- The original, unencrypted symmetric key is securely wiped from the computer's memory.
The genius of this method is that the data can only be decrypted by reversing the process. To do that, one needs the corresponding private key to decrypt the symmetric key. This private key is known only to the attacker and is safely stored on their remote server. Without it, there is no way to recover the symmetric key, and therefore no way to decrypt the file. It's like locking a diary in a box (symmetric encryption) and then locking the key to that box inside an unbreakable safe that only the attacker can open (asymmetric encryption).
The Extortion: Demanding the Ransom
With the victim's digital life now held hostage, the ransomware attack transitions from a technical assault to a psychological one. The extortion phase is where the attackers communicate their demands and apply intense pressure to force a payment. This is no longer about code and algorithms; it's about fear, panic, and a desperate cost-benefit analysis performed by the victim under extreme duress. The attackers' goal is to make paying the ransom seem like the quickest, easiest, and sometimes only path back to normalcy.
The primary tool of this phase is the ransom note. This isn't a discreet message; it's designed to be unmissable. It appears as a text file dropped in every encrypted folder, a pop-up window that can't be closed, or even as the new desktop wallpaper. The note is the attackers' direct line of communication, laying out the grim situation and the steps the victim must take to resolve it. The tone is typically cold, direct, and non-negotiable, designed to assert control and eliminate any hope of a simple fix.
Displaying the Ransom Note
The ransom note serves several purposes. First, it informs the victim of what has happened—that their files have been encrypted with strong cryptography. Second, it provides proof, often offering to decrypt one or two small files for free to demonstrate that the attackers do, in fact, possess the means of recovery. This builds a sliver of 'trust' in a trustless situation.
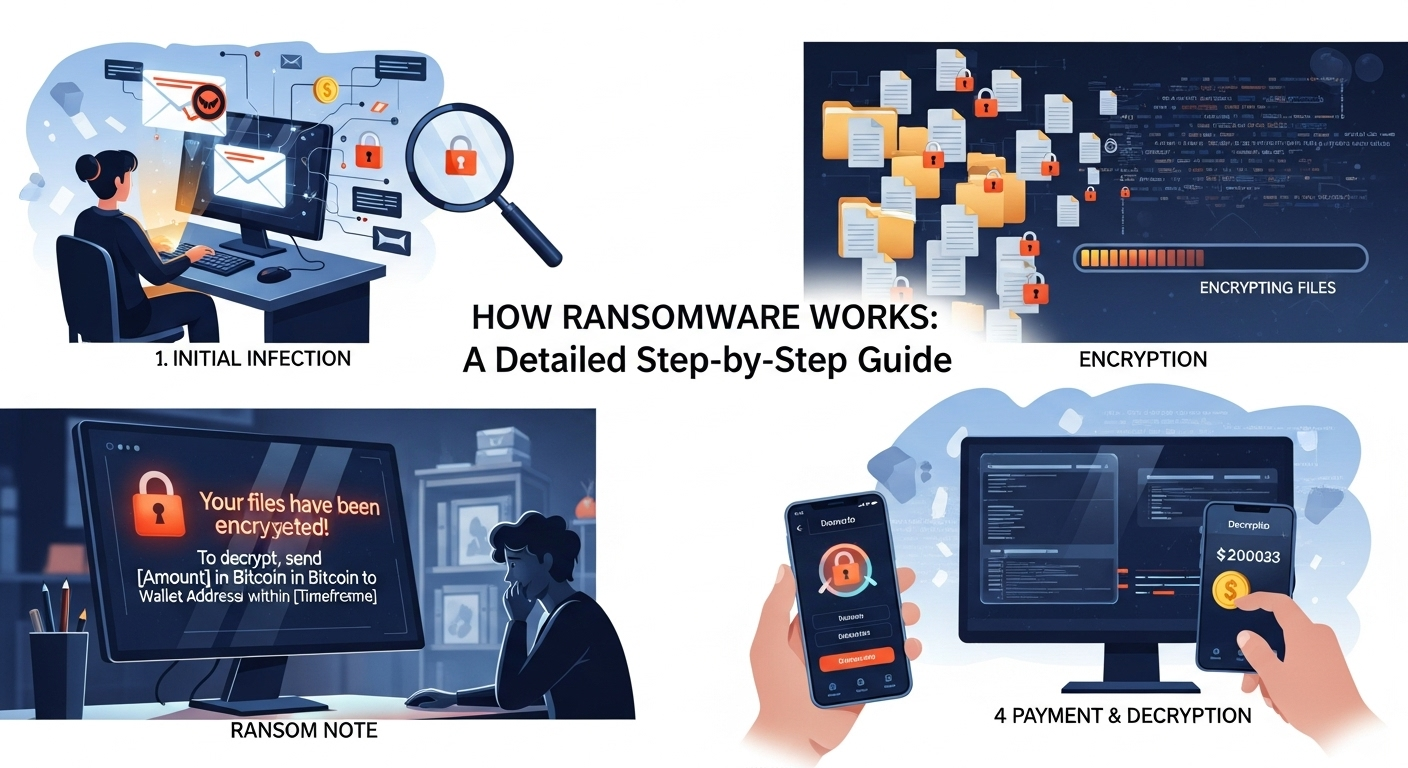
Most importantly, the note contains the core demands:
- The Ransom Amount: This can range from a few hundred dollars for an individual to millions for a large corporation. The currency is almost always a hard-to-trace cryptocurrency like Bitcoin (BTC) or Monero (XMR).
- The Payment Deadline: A countdown timer is a common psychological tactic. The note will state that if the payment is not made within a certain timeframe (e.g., 72 hours), the ransom amount will double, or the decryption key will be permanently deleted.
- Payment Instructions: The note provides detailed, step-by-step instructions on how to purchase cryptocurrency and transfer it to the attacker's digital wallet address.
The Payment and Communication Channel
To maintain anonymity, all communication and payment channels are routed through networks designed for privacy. The ransom note will often direct the victim to download the Tor browser, a tool that allows anonymous access to the "dark web." There, the victim will find a dedicated payment portal hosted on a `.onion` website. This portal is where they will enter their unique victim ID (provided in the ransom note), see the final ransom amount and wallet address, and potentially communicate with the attackers through a basic chat function.
This entire ecosystem is designed to be user-friendly for the panicked victim while being operationally secure for the attackers. The use of cryptocurrency makes the transaction pseudo-anonymous and extremely difficult for law enforcement to trace or reverse. The combination of a terrifying threat (permanent data loss), a ticking clock, and a clear, albeit criminal, path to resolution creates a powerful incentive to pay the ransom, despite official advice to the contrary.
The Aftermath and the Rise of a New Threat
The moment a ransomware attack is discovered, the victim is thrown into a crisis. The digital infrastructure is paralyzed, operations grind to a halt, and a critical decision must be made under immense pressure. The path forward is fraught with risk and uncertainty, regardless of the choice made. Whether the victim chooses to pay the ransom or attempt a recovery through other means, the aftermath is always costly, complex, and time-consuming.
In recent years, the landscape has become even more treacherous with the evolution of ransomware tactics. The initial model of simply encrypting files has been augmented by more sinister strategies designed to increase the attackers' leverage. The threat is no longer just about the availability of data, but also about its confidentiality. This has given rise to a new era of multi-layered extortion, making the decision-making process for victims even more agonizing.
The "To Pay or Not to Pay" Dilemma
The central question for any ransomware victim is whether to pay the ransom. Law enforcement agencies, including the FBI, strongly advise against paying. Their reasoning is threefold: first, paying the ransom directly funds criminal enterprises, enabling them to expand their operations and attack more victims. Second, it encourages more attacks by proving that ransomware is a profitable business model. Third, and most crucially, there is no guarantee that paying will result in the recovery of data. Attackers may fail to provide a working decryption key, provide a faulty decryptor that corrupts data, or simply disappear after receiving payment.
Despite this advice, many organizations choose to pay, viewing it as the fastest way to restore operations and avoid the potentially greater costs of prolonged downtime and manual data reconstruction. This decision is often influenced by the availability and quality of backups. If a company has recent, air-gapped backups that were unaffected by the attack, they have a viable path to recovery without paying. If their backups were also encrypted or destroyed, paying might feel like the only option left on the table.
The Rise of Double and Triple Extortion
Recognizing that robust backups could undermine their business model, ransomware gangs evolved. They pioneered a tactic known as double extortion. Before encrypting the files, the attackers first exfiltrate, or steal, large quantities of sensitive data from the victim's network. Now, they have two levers of extortion. The primary threat is still the encryption: "Pay us, or you'll never get your files back." The secondary, and often more powerful, threat is: "If you don't pay us, we will leak your sensitive data to the public."
This changes the entire calculation. Even if a company can restore from backups, the threat of a massive data breach—exposing customer information, employee records, trade secrets, and intellectual property—can be catastrophic. It can lead to regulatory fines (e.g., under GDPR), lawsuits, reputational damage, and a loss of customer trust. Some ransomware groups, such as REvil and Maze, created dedicated "leak sites" on the dark web where they would publish the data of non-compliant victims. This has been further escalated into triple extortion, where attackers also threaten to use the stolen information to attack the victim's clients or partners, or launch Denial-of-Service (DDoS) attacks against the victim's public-facing services until the ransom is paid.
Prevention and Mitigation: Your Best Defense
While understanding how ransomware works is crucial, the ultimate goal is to prevent it from happening in the first place. A reactive strategy is a losing strategy. A proactive and layered approach to cybersecurity is the only effective way to protect against this ever-evolving threat. This involves a combination of robust technical controls, disciplined processes, and a security-conscious culture where every user understands their role in defending the organization.
Defense-in-depth is the guiding principle here. This means implementing multiple layers of security, assuming that any single layer might fail. If a phishing email gets past the email filter, user training should prevent the click. If a user clicks, the endpoint protection should block the malware. If the malware executes, an immutable backup should make recovery possible without paying the ransom. No single solution is a silver bullet; strength comes from the integration of multiple defensive measures.
| Attack Phase | Primary Defense Strategy | Key Tools and Practices |
|---|---|---|
| Initial Breach | Reduce the Attack Surface | • Email Filtering & Anti-Phishing<br>• Regular Software Patching<br>• Multi-Factor Authentication (MFA) |
| Infection & Establishment | Detect & Block Malicious Activity | • Next-Gen Antivirus (NGAV)<br>• Endpoint Detection & Response (EDR)<br>• Principle of Least Privilege (PoLP) |
| Encryption | Isolate & Contain the Threat | • Network Segmentation<br>• Monitoring for mass file changes<br>• Automated threat response |
| Extortion & Aftermath | Ensure Resilience & Recovery | • The 3-2-1 Backup Rule (offline/immutable)<br>• Incident Response (IR) Plan<br>• Regular backup testing |
Proactive Technical Defenses
The foundation of ransomware prevention lies in strong technical controls. This starts with prompt patch management. Regularly updating all software—operating systems, applications, and firmware—closes the vulnerabilities that attackers love to exploit. Coupled with this is the enforcement of strong, unique passwords and, most importantly, Multi-Factor Authentication (MFA) wherever possible. MFA adds a critical layer of security that can stop an attacker even if they have stolen a user's password.
Furthermore, a modern security stack is essential. This includes advanced email filtering to block phishing attempts before they reach a user's inbox, and a Next-Generation Antivirus (NGAV) or Endpoint Detection and Response (EDR) solution on all devices. Unlike traditional antivirus that relies on known signatures, these advanced tools use behavioral analysis and machine learning to detect and block suspicious activities indicative of a ransomware attack in progress.
The Power of Backups and a Recovery Plan
The single most effective tool for recovering from a ransomware attack is a reliable and recent backup. However, not all backups are created equal. Attackers know that backups are their biggest enemy, so they actively hunt for and delete them. An effective backup strategy must account for this. The industry best practice is the 3-2-1 Rule:
- 3 copies of your data.
- 2 different types of media (e.g., local disk and cloud).
- 1 copy stored off-site and offline/air-gapped or in immutable storage.
This final point is the most critical. An offline or immutable backup is one that the ransomware cannot access or modify, ensuring you have a clean copy of your data for restoration. Just as important as having backups is regularly testing them to ensure they can be successfully restored. A backup that fails to restore is no better than no backup at all.
Cultivating a Security-Aware Culture
Technology alone is not enough. Since social engineering is the number one vector for ransomware, the human element is often the weakest link. Therefore, continuous security awareness training for all users is non-negotiable. Employees must be trained to recognize the signs of a phishing email, to be suspicious of unsolicited attachments and links, and to know how to report a potential threat.
This training should be reinforced with regular phishing simulations to test and measure user awareness. The goal is not to punish users who fail, but to create a culture of vigilance and shared responsibility for security. When users see themselves as a vital part of the organization's defenses, the human firewall becomes one of its strongest assets.
—
Frequently Asked Questions (FAQ)
Q: Can I get my files back without paying the ransom?
A: Sometimes, but it's not common. In rare cases, a flaw in the ransomware's encryption code may be discovered, and security researchers may release a free decryptor tool. Websites like the No More Ransom Project compile these tools. However, for most modern ransomware variants, the encryption is too strong to break. The most reliable way to get files back without paying is by restoring them from a clean, unaffected backup.
Q: Does paying the ransom guarantee I get my files back?
A: No, it does not. While many ransomware gangs run their operations like a business and will provide a decryptor to maintain their "reputation," there are significant risks. The decryptor tool they provide could be buggy and corrupt some or all of the files during the decryption process. In other cases, the attackers may simply take the money and provide nothing. The FBI reports that even when victims pay, they don't always get all their data back.
Q: What is the very first thing I should do if I am hit by ransomware?
A: Isolate the infected device immediately. Disconnect it from the network (unplug the ethernet cable, turn off Wi-Fi) and disconnect any attached external drives. This can prevent the ransomware from spreading to other computers on the network or encrypting your backups. After isolation, do not turn off or reboot the machine unless instructed by a cybersecurity professional, as this can sometimes erase forensic evidence. Then, immediately contact your IT department or a professional incident response team.
Q: Why do attackers demand payment in cryptocurrency like Bitcoin?
A: Attackers use cryptocurrencies for two main reasons: anonymity and irreversibility. Cryptocurrencies like Bitcoin and Monero are decentralized and can be transferred across borders without involving traditional banks, making them very difficult for law enforcement to track. Once a transaction is confirmed on the blockchain, it is permanent and cannot be reversed or charged back, ensuring the attackers get to keep their illicit gains.
—
Conclusion
Ransomware is more than just malware; it is a meticulously orchestrated criminal enterprise that exploits weaknesses in technology, processes, and human psychology. From the initial deceptive phish to the high-pressure extortion tactics, every step is designed to corner the victim and force a payment. As we have seen, the attack lifecycle is a multi-stage process involving infiltration, establishing control, encrypting valuable data, and finally, demanding a ransom under threat of permanent loss or public data exposure.
While the threat is formidable, it is not invincible. The key to defense lies in a proactive, multi-layered strategy. By hardening technical defenses, maintaining pristine and isolated backups, and fostering a vigilant, security-aware culture, organizations and individuals can build a resilient posture. Understanding how ransomware works is the first step—not to induce fear, but to empower action. In the ongoing battle against cybercrime, knowledge and preparation are your most powerful weapons.
***
Article Summary
This article, "How Ransomware Works: A Detailed Step-by-Step Guide," provides a comprehensive analysis of the entire ransomware attack lifecycle. It begins by explaining the initial breach methods, focusing on phishing/social engineering, the exploitation of unpatched software vulnerabilities, and attacks on insecure Remote Desktop Protocol (RDP). The guide then details the second phase, where the malware establishes persistence on the system, escalates its privileges, and disables security measures like antivirus and backups.
The core of the article breaks down the encryption process, explaining how modern ransomware uses a hybrid of symmetric (AES) and asymmetric (RSA) cryptography to lock files, making them impossible to decrypt without the attacker's private key. The extortion phase is then covered, detailing how attackers use ransom notes, countdown timers, and anonymous payment portals on the Tor network to demand payment in cryptocurrency. The article also explores the evolution of the threat into double and triple extortion, where attackers steal data before encrypting it and threaten to leak it publicly. Finally, it concludes with actionable prevention strategies, emphasizing the importance of a layered defense that includes technical controls (like MFA and patching), the 3-2-1 backup rule with offline copies, and continuous user security awareness training. An FAQ section addresses common victim concerns, solidifying the article as a practical resource for understanding and combating ransomware.