In an era where the traditional office has expanded to include living rooms, coffee shops, and co-working spaces across the globe, the conversation around digital security has never been more critical. The flexibility of remote work brings undeniable benefits, but it also opens up a new frontier of vulnerabilities that cybercriminals are eager to exploit. Protecting sensitive company data and personal information is no longer just the IT department's responsibility; it's a crucial part of every remote worker's daily routine. This is where a robust VPN for remote work security transitions from a "nice-to-have" tech accessory to an absolutely essential tool for professional survival and integrity. Understanding the 'Why': The Critical Need for VPNs in a Remote World The global shift towards remote and hybrid work models is not a fleeting trend but a permanent evolution in the professional landscape. Companies and employees alike have embraced the autonomy and efficiency it offers. However, this distributed workforce model fundamentally alters the security perimeter. Instead of a single, fortified office network, companies now rely on dozens, hundreds, or even thousands of individual, often unsecured, home networks. This decentralization creates a significantly larger attack surface for malicious actors. Each remote worker's connection is a potential gateway into the corporate network. Home Wi-Fi routers, often configured with default passwords and outdated firmware, are low-hanging fruit for hackers. Public networks, like those found in cafes or airports, are even more perilous, acting as hunting grounds for data thieves. Without a protective layer, every email sent, every file downloaded, and every password entered while connected to these networks is at risk of interception. The potential consequences range from individual identity theft to catastrophic corporate data breaches, costing millions in damages and eroding customer trust. This is precisely the problem a Virtual Private Network (VPN) is designed to solve. It acts as a secure, encrypted tunnel for your internet traffic, shielding it from prying eyes. By routing your connection through a private server, a VPN makes your online activities invisible to anyone on the same network, including cybercriminals, your Internet Service Provider (ISP), and opportunistic snoopers. For a remote workforce, a VPN isn't just about privacy; it's a foundational pillar of a secure and resilient remote work infrastructure, ensuring that business can continue securely, no matter where an employee logs on. What is a VPN and How Does it Bolster Remote Work Security? At its core, a VPN is a service that creates a secure and encrypted connection over a less secure network, such as the public internet. Imagine you are sending a valuable package through the mail. Without a VPN, it’s like sending that package in a clear, unlocked box. Anyone who handles it can see what’s inside and even tamper with it. Using a VPN is like placing that package inside a locked, opaque steel safe before mailing it. The safe (the VPN tunnel) travels through the same postal system (the internet), but no one can see what's inside or access its contents until it reaches its intended recipient with the correct key. This "digital safe" is created through two key processes: tunneling and encryption. Tunneling encapsulates your data packets within other packets before sending them across the internet. This creates a private 'tunnel' through the public network. More importantly, everything inside this tunnel is encrypted. This means the data is scrambled into an unreadable code. Even if a hacker managed to intercept your data, they would only see a jumble of nonsensical characters without the specific decryption key, which resides only on your device and the VPN server. A VPN also masks your real IP address, replacing it with the IP address of the VPN server you connect to, further anonymizing your online presence and location. For remote workers, the practical applications of this technology are immense. When you connect to your company’s servers to access sensitive files, a VPN ensures that the connection is completely private and secure, preventing man-in-the-middle attacks. When you're working from a hotel with notoriously insecure Wi-Fi, a VPN encrypts your entire session, protecting your login credentials, client communications, and proprietary data. It essentially recreates the security of a physical office network, allowing you to work from anywhere with confidence and peace of mind. The Core Components of VPN Security The strength of a VPN is determined by its underlying technology, primarily its encryption standards and tunneling protocols. These elements work in tandem to create the secure environment necessary for remote work. Understanding them helps in differentiating a robust, enterprise-grade VPN from a flimsy, consumer-grade one that offers a false sense of security. The gold standard for encryption today is AES (Advanced Encryption Standard) 256-bit encryption. This is the same level of encryption used by governments, militaries, and financial institutions worldwide to protect top-secret information. It is, for all practical purposes, unbreakable by brute force. When a VPN service advertises AES-256, it means your data is being scrambled with a key of such complexity that it would take the world's most powerful supercomputers billions of years to crack. For remote work security, settling for anything less is an unnecessary risk. Tunneling Protocols: The Highways of Your Data Tunneling protocols are the sets of rules that determine how your data tunnel is built and maintained. Different protocols offer varying balances of speed, stability, and security. OpenVPN is a highly versatile and secure open-source protocol, long considered the industry standard for its reliability. IKEv2/IPsec is known for its stability and speed, especially on mobile devices, as it can re-establish a connection quickly if you switch between Wi-Fi and cellular data. The newest major protocol, WireGuard, is a game-changer, offering blazing-fast speeds and top-tier security with a much leaner codebase, making it easier to audit and less prone to vulnerabilities. A quality VPN provider will offer a choice of these protocols to suit different needs. Essential Features Beyond the Basics Beyond core encryption and protocols, several features are non-negotiable for anyone serious about VPN for remote work security. A Kill Switch
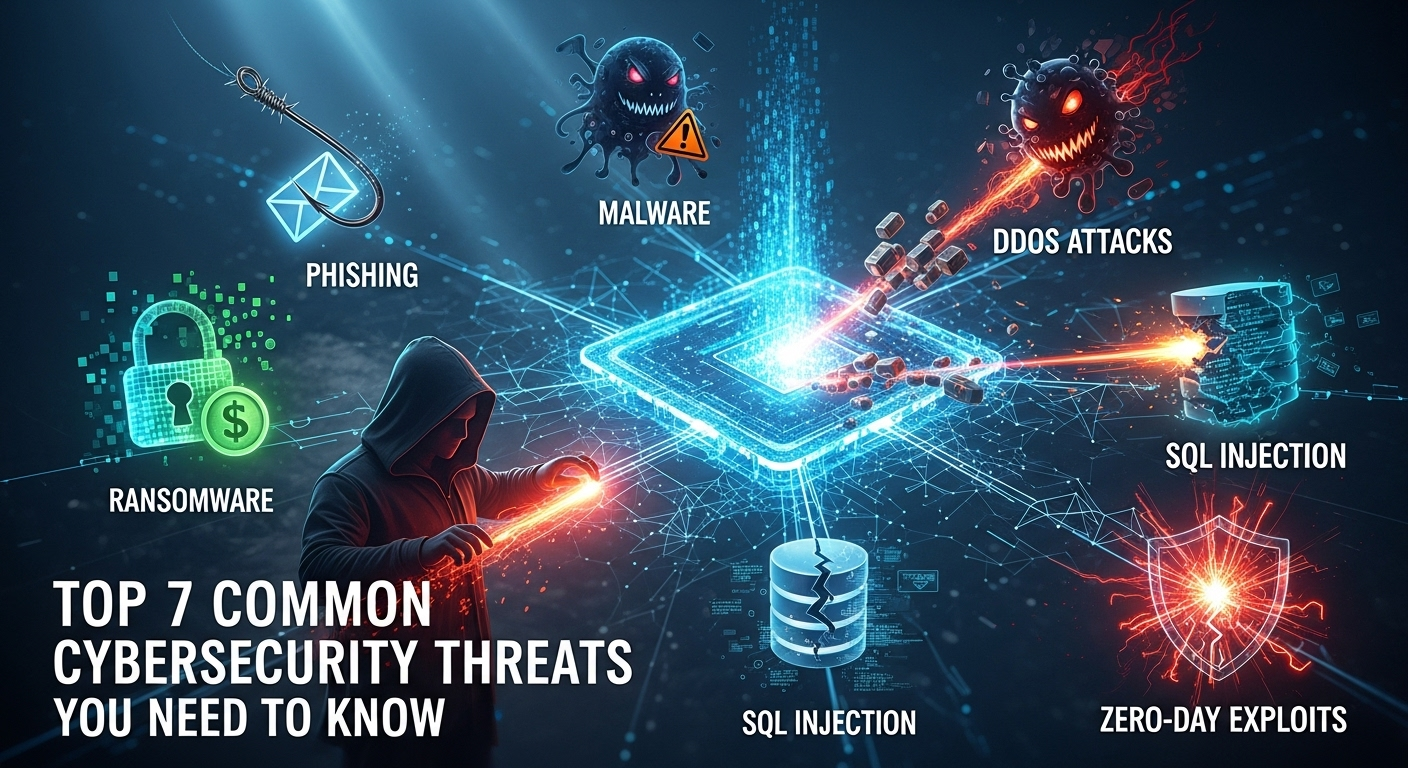
Top 7 Common Cybersecurity Threats You Need to Know
In today's hyper-connected world, our personal and professional lives are inextricably linked to the digital realm. From online banking and social media to cloud storage and remote work, we rely on a vast network of systems that, while offering unprecedented convenience, also expose us to a growing number of risks. Understanding the types of common cybersecurity threats is no longer a task reserved for IT professionals; it's a fundamental aspect of modern literacy. Failing to recognize these dangers can lead to devastating consequences, including financial loss, identity theft, and significant business disruption. This guide will demystify the digital shadows, breaking down the most prevalent threats you need to be aware of to protect your digital life. Phishing: The Art of Digital Deception Phishing remains one of the most pervasive and effective cybersecurity threats, primarily because it targets the weakest link in any security chain: a human being. At its core, phishing is a form of social engineering where an attacker masquerades as a legitimate entity—such as a bank, a popular online service, or even a colleague—to trick a victim into divulging sensitive information. This can include login credentials, credit card numbers, or personal identifiers. The attack is typically initiated through an email, text message (known as smishing), or instant message that creates a sense of urgency, fear, or curiosity to prompt immediate action. The sophistication of phishing attacks has evolved dramatically. Early attempts were often riddled with grammatical errors and were easy to spot. Today, attackers can create pixel-perfect replicas of legitimate websites and craft highly convincing email templates. They often employ advanced techniques like spear phishing, which is a targeted attack on a specific individual or organization, using personal information to make the lure more believable. A more targeted form, whaling, aims for high-profile targets like C-suite executives who have access to highly valuable company data. Attackers might reference a recent company event or a project the target is working on, making the fraudulent request seem entirely legitimate. Protecting yourself from phishing requires a combination of technological aids and, more importantly, a vigilant mindset. Modern email filters are adept at catching a large volume of spam and phishing attempts, but some will always slip through. Therefore, it's crucial to cultivate a healthy skepticism toward unsolicited communications. Always scrutinize the sender's email address, hover over links to see the actual destination URL before clicking, and be wary of any message that demands urgent action or asks for personal information. For organizations, implementing Multi-Factor Authentication (MFA) is one of the most effective defenses, as it requires a second form of verification even if an attacker manages to steal a password. Malware: Malicious Software in Your System Malware, a portmanteau of "malicious software," is an umbrella term that encompasses any software intentionally designed to cause damage to a computer, server, client, or computer network. It is a workhorse of cybercrime, used to steal data, disrupt operations, and provide attackers with a foothold into a secure network. Malware can find its way onto a system through various vectors, including deceptive email attachments, malicious downloads from untrustworthy websites, or even bundled with seemingly legitimate software. Once executed, it can operate silently in the background, making it difficult to detect without dedicated security tools. There are several distinct categories of malware, each with a different objective: Viruses: Like their biological counterparts, computer viruses attach themselves to clean files and spread from one file to another, infecting the system. They require a host program to run. Worms: Unlike viruses, worms are standalone pieces of software that can replicate themselves and spread across networks without human intervention, often by exploiting vulnerabilities. Trojans: Named after the mythical Trojan Horse, this type of malware disguises itself as a legitimate or useful piece of software. Once inside, it can perform malicious actions, such as creating a backdoor for an attacker, installing other malware, or stealing data. <strong>Spyware:</strong> This malware is designed to spy on you. It secretly records your actions, such as keystrokes (keyloggers*), browsing history, and login credentials, and sends this information back to the attacker. Perhaps the most notorious and feared type of malware in recent years is ransomware. This malicious software encrypts a victim's files, rendering them completely inaccessible. The attacker then demands a ransom payment, typically in cryptocurrency like Bitcoin, in exchange for the decryption key. High-profile examples like WannaCry and Ryuk have caused billions of dollars in damages, crippling hospitals, city governments, and multinational corporations. The threat has also evolved into "double extortion," where attackers not only encrypt the data but also exfiltrate it, threatening to publish it online if the ransom isn't paid. This puts immense pressure on organizations to comply with the demands. Man-in-the-Middle (MitM) Attacks: The Digital Eavesdropper A Man-in-the-Middle (MitM) attack is a form of digital eavesdropping where an attacker secretly intercepts and potentially alters the communication between two parties who believe they are communicating directly with each other. Imagine trying to have a private conversation, but an impostor is intercepting your messages, reading them, and then passing them along, possibly after changing their contents. This is precisely what happens in a MitM attack. The primary goal is to steal personal information, such as login credentials, credit card details, or business secrets, as it is being transmitted. The most common environment for MitM attacks is on unsecured public Wi-Fi networks, like those found in coffee shops, airports, and hotels. An attacker can set up their own malicious Wi-Fi hotspot with a convincing name (e.g., "FreeAirportWiFi") in a technique known as an "evil twin" attack. When users connect to it, the attacker can monitor all their unencrypted internet traffic. They can redirect victims to fraudulent versions of websites to capture login details or inject malicious code directly into the web pages they visit. Preventing MitM attacks involves being cautious about the networks you connect to and ensuring your data is encrypted in transit. The most reliable way to secure your connection, especially on public Wi-Fi, is by using a Virtual Private
What Is a VPN and How Does It Work? A Simple Guide
Have you ever used a public Wi-Fi network at a café or airport and worried about the security of your data? Or perhaps you've tried to watch your favorite show while traveling, only to be met with a frustrating "content not available in your region" message. These common digital-age problems have a powerful and increasingly popular solution: the VPN. But this then raises the crucial question for anyone looking to bolster their online freedom and security: what is a vpn and how does it work? This simple guide will demystify the technology, breaking down its complex mechanics into easy-to-understand concepts, and show you why it's becoming an essential tool for internet users everywhere. What Is a VPN? A Deeper Look Beyond the Acronym At its core, VPN stands for Virtual Private Network. The name itself provides a great clue to its function. It creates a virtual, encrypted tunnel for your internet traffic, giving you a private connection even when you are using a public or shared network. Think of it as building a secure, private highway for your data that runs directly through the chaotic and public city streets of the internet. Instead of your data being exposed to potential onlookers—like your Internet Service Provider (ISP), hackers, or advertisers—it is safely enclosed within this tunnel from the moment it leaves your device until it reaches its final destination. The primary purpose of a VPN is to enhance your privacy and security online. It achieves this by doing two main things: masking your real IP address and encrypting your entire internet connection. Your IP (Internet Protocol) address is a unique numerical label assigned to your device, much like a physical mailing address for your home. It reveals your geographic location and can be used to track your online activities. A VPN replaces your IP address with one from its own server, making it appear as if you are browsing from a completely different location. This, combined with powerful encryption, makes your digital footprint significantly more anonymous and secure. It's important to distinguish a VPN from a proxy server, as they are often confused. While both can reroute your traffic and change your IP address, a VPN offers a far more comprehensive security solution. A typical proxy server only works on an application-by-application basis (e.g., just for your web browser) and often does not encrypt your traffic. A VPN, on the other hand, operates at the operating system level. This means it captures and encrypts all internet traffic from your device—whether it's from your browser, a gaming app, your email client, or a background update. This holistic protection is what makes a VPN a superior tool for overall digital security and privacy. The Core Mechanics: How Does a VPN Work? Understanding how a VPN functions doesn't require a degree in computer science. The process can be broken down into a logical sequence of steps that transform your insecure, public connection into a secure, private one. It all begins when you activate the VPN application on your computer, smartphone, or tablet. You select a server from a list—which could be in your own country or halfway across the world—and click "connect." In just a few seconds, your entire online experience is fundamentally changed, operating under a powerful shield of digital protection. The magic happens through a combination of encryption and tunneling. When you connect to the VPN, the software on your device (the VPN client) establishes a secure connection with the VPN server you selected. This connection is called a secure tunnel. Before any data—such as the website you want to visit or an email you're sending—leaves your device, the VPN client encrypts it. This means it scrambles the data into an unreadable code using complex algorithms. This encrypted data then travels through the secure tunnel, passing through your local network and your ISP, who can see that you are connected to a VPN but cannot see the content of your data or your final destination. Once your encrypted data reaches the VPN server, it is decrypted. The VPN server then forwards your request to the final destination on the public internet (e.g., `google.com` or `netflix.com`). The website or service you are accessing sees the request as coming from the VPN server, not from your personal device. It therefore sees the VPN server's IP address and location, not your own. The website then sends the data back to the VPN server, which encrypts it again and sends it back to your device through the secure tunnel. Your VPN client decrypts the data, and you see the webpage load as normal. This entire round-trip process happens in milliseconds, providing a seamless yet highly secure browsing experience. 1. The Encryption Process: Securing Your Data Encryption is the bedrock of VPN security. It is the process of converting your readable data (plaintext) into a scrambled, unintelligible format (ciphertext) using a cryptographic key. Only someone with the correct key can decrypt the data and turn it back into its original, readable form. Modern VPNs use highly sophisticated encryption standards, with AES (Advanced Encryption Standard) 256-bit being the industry benchmark. To put its strength into perspective, this is the same level of encryption used by governments and security agencies around the world to protect classified information. It is considered computationally infeasible to crack with current technology. This robust encryption is precisely what protects you from various online threats. On an unsecured public Wi-Fi network, a cybercriminal could position themselves between you and the connection point in what's known as a man-in-the-middle attack. Without a VPN, they could easily intercept your unencrypted data, capturing sensitive information like passwords, credit card details, and private messages. With a VPN enabled, any data they might intercept would be just a stream of nonsensical ciphertext, rendering it completely useless to them. This ensures your private information remains private, no matter how insecure the network you're using is. 2. Tunneling Protocols: The Highway for Your Data While encryption scrambles your data, tunneling protocols
Understanding the Basics of Network Security: A Guide
In an age where our lives—personal and professional—are inextricably linked to the digital world, the invisible infrastructure that connects us has become a prime target for malicious actors. From multinational corporations to a family's smart home devices, everything relies on a network to communicate. Consequently, understanding the basics of network security is no longer a niche skill for IT professionals but a fundamental necessity for anyone navigating the online landscape. This guide is designed to demystify the core concepts, threats, and best practices, providing a solid foundation for protecting your digital assets in an increasingly connected world. What is Network Security and Why is it Crucial? Network security is a broad term that encompasses a multitude of technologies, devices, and processes. In essence, it refers to any activity designed to protect the usability, reliability, integrity, and safety of a network and its data. It involves a combination of hardware and software solutions, as well as policies and procedures, all working in concert to prevent unauthorized access, misuse, modification, or denial of the network and its resources. Think of it as the digital equivalent of securing a physical building with locks, security guards, alarm systems, and access protocols. The importance of network security cannot be overstated. A security breach can lead to catastrophic consequences, including the theft of sensitive data like personal information, financial records, and intellectual property. For businesses, this can result in devastating financial losses, regulatory fines (such as those under GDPR or CCPA), and a severe blow to their reputation. For individuals, a compromised network can lead to identity theft, financial fraud, and a profound loss of privacy. In a world driven by data, protecting the network is synonymous with protecting the very foundation of modern communication and commerce. Furthermore, the threat landscape is constantly evolving. Cybercriminals are becoming more sophisticated, leveraging advanced tools and techniques, including artificial intelligence, to launch attacks. Threats are no longer limited to simple viruses; they now include complex ransomware, stealthy spyware, and large-scale Distributed Denial-of-Service (DDoS) attacks. This dynamic environment makes a proactive and layered approach to network security absolutely essential for survival and success. The CIA Triad: The Cornerstone of Security At the heart of all information security, including network security, lies a foundational model known as the CIA Triad. This acronym stands for Confidentiality, Integrity, and Availability. These three principles form a benchmark for evaluating and establishing a robust security posture. A failure in any one of these areas constitutes a security breach. Confidentiality: This principle ensures that information is not disclosed to unauthorized individuals, entities, or processes. It's about data privacy and preventing sensitive information from falling into the wrong hands. Encryption is a primary tool for ensuring confidentiality, as it scrambles data so that only authorized parties with the correct key can read it. Access controls, such as passwords and biometric verification, also play a vital role. Integrity: This principle guarantees that data is trustworthy and has not been tampered with or altered by unauthorized parties. It's about maintaining the accuracy and consistency of data throughout its lifecycle. Hashing algorithms are often used to verify data integrity. For example, when you download a file, a checksum or hash value may be provided, allowing you to confirm that the file you received is identical to the original and hasn't been corrupted or maliciously modified. Availability: This principle ensures that authorized users have reliable and timely access to network resources and data. An unavailable network can halt business operations, cut off communication, and prevent access to critical services. Threats to availability include hardware failures, software bugs, and malicious attacks like Denial-of-Service (DoS), which are specifically designed to make a system or network inaccessible. Redundancy, regular maintenance, and disaster recovery plans are key to upholding this principle. The Cost of Insecurity Many individuals and small businesses operate under the dangerous assumption that they are "too small to be a target." This could not be further from the truth. In reality, smaller entities are often seen as softer targets due to their typically weaker security measures. The cost of a security breach extends far beyond the immediate financial impact of stolen funds or data. The direct financial costs are often staggering. These can include the cost of remediation (hiring experts to clean up the mess), regulatory fines for non-compliance with data protection laws, legal fees, and potential ransom payments in the case of a ransomware attack. According to IBM's Cost of a Data Breach Report 2023, the global average cost of a data breach reached an all-time high of $4.45 million. These figures highlight that investing in security is not a cost center, but a critical investment in risk mitigation. Beyond the measurable financial loss is the often-irreparable damage to an organization's reputation. Customer trust is hard-earned and easily lost. When a company fails to protect its customers' data, that trust is shattered. The resulting customer churn, negative press, and damage to the brand can have long-lasting effects that far outweigh the initial financial costs of the breach itself. Rebuilding a tarnished reputation can take years, if it's even possible at all. — Core Components of a Secure Network Building a secure network is not about finding a single magic bullet. Instead, it relies on a strategy known as "defense in depth." This layered security approach assumes that any single defense mechanism can and will eventually fail. By implementing multiple layers of security controls, an organization can ensure that if an attacker bypasses one layer, they are immediately confronted by another, slowing them down and increasing the chances of detection. These layers consist of a mix of physical, technical, and administrative controls. Physical controls include locked server rooms, while administrative controls involve security policies and employee training. The technical controls are the hardware and software components that actively monitor and protect the network. A well-designed network security architecture integrates these components seamlessly to create a formidable barrier against threats. It is crucial to understand that these components are not "set and
How a VPN Connection is Established: A Simple Guide
In an age where our lives are increasingly intertwined with the digital world, the concepts of online privacy and security have shifted from niche concerns to mainstream necessities. Every click, search, and transaction sends data packets flying across the public internet, a space akin to a bustling public square where conversations can be overheard. This is where a Virtual Private Network, or VPN, becomes an indispensable tool. But have you ever stopped to wonder about the intricate digital dance that happens in the seconds after you click "Connect"? Understanding how a VPN connection is established is the key to appreciating the powerful protection it provides. This guide will demystify the process, breaking down the complex steps of authentication, tunneling, and encryption into a simple, step-by-step journey. The Foundations: What is a VPN and Why Do You Need One? At its core, a Virtual Private Network (VPN) is a service that creates a secure and encrypted connection over a less secure network, such as the public internet. The best way to visualize this is to imagine the internet as a vast, open highway system. Without a VPN, your data travels on this highway in a clear glass car, allowing your Internet Service Provider (ISP), network administrators, and potential bad actors to see where you're going and what you're carrying. A VPN, however, builds a private, opaque tunnel for your car. Inside this tunnel, your vehicle is invisible, and its contents are locked in an unbreakable safe. The primary purpose of a VPN is to enhance your privacy, security, and anonymity online. Security is achieved through robust encryption, which scrambles your data, making it completely unreadable to anyone who might intercept it. This is particularly crucial when using public Wi-Fi networks in places like cafes, airports, or hotels, which are notorious hotspots for cybercriminals looking to steal sensitive information like passwords and credit card details. Privacy is preserved by masking your true IP address—your unique identifier on the internet—and replacing it with the IP address of the VPN server. This prevents websites, advertisers, and even your ISP from tracking your online activities and building a profile based on your browsing habits. The practical applications of this technology are vast and varied. For remote workers, a VPN is essential for securely accessing a company's internal network and sensitive files from home or while traveling, ensuring that confidential business data remains protected. For the everyday user, it's a powerful tool for bypassing geo-restrictions, allowing you to access content and services that might be unavailable in your region. By connecting to a server in a different country, you can effectively "teleport" your digital location, unlocking international streaming libraries or accessing websites that are blocked locally. Ultimately, a VPN gives you greater control over your digital footprint and restores a measure of freedom and privacy to your online experience. The First Handshake: Authentication and Authorization The very first step in establishing a VPN connection is a digital "handshake" known as authentication and authorization. This process is all about verification. Before a secure tunnel can be built, the VPN server needs to confirm two critical things: first, that you are who you say you are (authentication), and second, that you have the right to use the service (authorization). This initial phase is initiated the moment you open your VPN application and click the "Connect" button. Your device's VPN client immediately sends a connection request to the VPN server you've selected. Authentication is the process of proving your identity. In most cases, this is handled through a username and password that you created when you signed up for the VPN service. When your VPN client contacts the server, it presents these credentials. The server then cross-references this information with its database of registered users. This is analogous to a security guard checking your photo ID against a guest list before letting you into an exclusive event. Some more advanced systems might use digital certificates or multi-factor authentication (MFA) for an even higher level of security, requiring a second form of verification, such as a code sent to your phone. Once your identity has been successfully authenticated, the server moves on to authorization. This step confirms that your account is in good standing and has permission to establish a connection. The server checks details like whether your subscription is active and paid for, or if your account has been flagged for any violations of the terms of service. If both authentication and authorization are successful, the server gives the green light to proceed to the next stage: building the secure tunnel. If either step fails, the connection is immediately terminated, and your VPN client will typically display an error message. #### The Role of Your VPN Client The VPN client is the software application you install on your computer, smartphone, or another device. It serves as the command center for your VPN connection, acting as the crucial intermediary between you and the VPN server. This software is responsible for storing your login credentials securely and presenting them to the server during the authentication phase. It also houses the necessary configurations and protocols required to initiate and maintain a stable connection. When you select a server location and hit "Connect," it's the client's job to package this request and send it out over the internet. This isn't just a simple message; it's a carefully structured communication packet that tells the server your identity and your intent to build a secure tunnel. The client handles the complexities of this initial negotiation, ensuring that it speaks the same "language" as the server to facilitate a smooth and successful handshake. #### Server-Side Verification On the other end of the initial request is the VPN server, a powerful computer located somewhere in the world, waiting for connection requests from clients. When your request arrives, the server’s software immediately begins its verification process. It unpacks the data packet sent by your client and extracts the authentication credentials. The server's primary task here is to
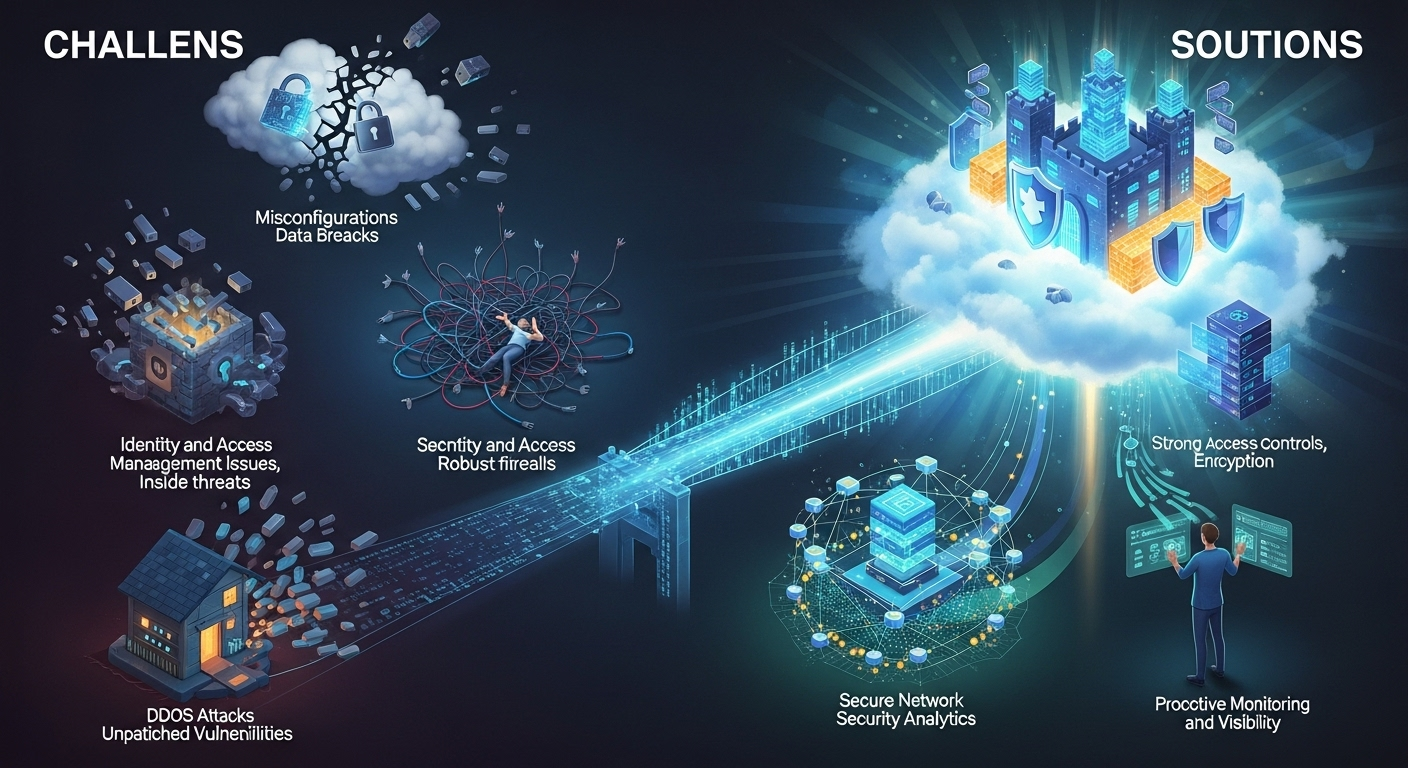
Common Cloud Security Challenges and How to Solve Them
Organizations are accelerating cloud adoption to gain agility, reduce costs, and innovate faster—but the attack surface expands just as quickly. From misconfigurations and identity sprawl to visibility blind spots and compliance drift, the common cloud security challenges can feel relentless. The good news: with the right architecture, controls, and culture, you can turn the cloud into a security advantage rather than a liability. Why Cloud Security Is Different in 2025 and Beyond Cloud security is not just “datacenter security in someone else’s building.” The cloud is API-driven, elastic, and shared by design. Those qualities boost speed and resilience, yet they also create new pathways for mistakes and misuse. Security teams must adapt to ephemeral infrastructure, declarative tooling, and continuous delivery rhythms that don’t pause for manual approvals. Unlike traditional environments, cloud assets change minute-to-minute: instances scale up and down, containers are rescheduled, serverless functions spin up on request, and identities (both human and machine) multiply. In this dynamic world, spreadsheets and one-time audits fall short. You need continual assurance, policy-as-code, and automated guardrails that enforce intent at scale. Another difference is the shared responsibility model. Your cloud service provider (CSP) secures the underlying infrastructure, but you remain responsible for how you configure services, manage identities, encrypt data, and monitor activity. Misunderstanding this division remains a top root cause of breaches. Treat the cloud as a co-managed ecosystem where accountability is explicitly defined and tested. The Shared Responsibility Reality Many organizations assume their CSP “handles security.” In reality, providers protect the physical data centers, the hypervisors, and certain managed services, while customers must secure data, identities, configurations, and application code. Failure to delineate duties—especially in multi-cloud—creates coverage gaps. To avoid surprises, document a responsibility matrix per service (e.g., IaaS, PaaS, SaaS) and per control (encryption, logging, patching, backup). Then validate it via continuous control monitoring (CCM). Clear accountability ensures that when auditors ask “who owns what,” you have a defensible, current answer rather than a best guess. Ephemeral and API-First Stacks Cloud-native stacks are de facto API-first. Every action—from provisioning to security changes—can be automated. This is powerful, but it also means a single misconfigured template can replicate risk across thousands of resources in seconds. Traditional change boards can’t keep pace. Embrace infrastructure as code (IaC) with pre-commit security checks, verified modules, and drift detection. This way, your “secure default” templates are reused and tested, not re-invented under pressure. When security becomes code, it scales with your engineering velocity. Challenge #1: Misconfigurations and Shared Responsibility Gaps Misconfiguration is the most pervasive cloud risk. Public S3 buckets, open security groups, overly permissive IAM policies, and disabled logging are frequent culprits. Because cloud controls are granular and plentiful, it’s easy to make a small mistake that has large blast radius. This challenge is amplified in multi-account/multi-subscription setups. Each environment—dev, test, prod—often has different controls, inherited policies, and exceptions. Without centralized policy evaluation and consistent baselines, “snowflake” environments drift out of compliance. Finally, misunderstanding shared responsibility leads to unclear handoffs. Who ensures KMS keys rotate? Who remediates public snapshots? Without clarity, issues persist. Adopt a culture of “secure by default” where guardrails prevent misconfigurations from ever deploying. Typical Missteps to Watch Common pitfalls include: Storage exposed to the public internet. Overly broad IAM roles (e.g., “:” permissions). Disabled or incomplete logging (e.g., missing flow logs). Unencrypted data at rest or in transit. Inconsistent tag governance, making assets hard to track. Each misstep seems small in isolation, but attackers chain them together. For example, a leaked access key with broad permissions plus missing logs equals stealthy exfiltration. Secure the small stuff, and you prevent the big breach. How to Fix with CSPM and Guardrails Use Cloud Security Posture Management (CSPM) to continuously detect misconfigurations across accounts and regions. Pair it with policy-as-code to enforce mandatory controls (e.g., deny public storage unless explicitly approved). Automate remediation where safe—quarantine public buckets, fix security groups, or enable logging as a default. Complement CSPM with IaC scanning in CI/CD. By shifting left, you catch risky patterns before deployment. Over time, measure “mean time to remediate (MTTR) misconfigurations” and “percentage of resources governed by guardrails” to ensure your posture is actually improving. Challenge #2: Identity, Access, and Zero Trust at Scale In the cloud, identity is the new perimeter. You’ll juggle human users, service principals, roles, short-lived tokens, and workload identities across multiple clouds. Over-privilege is common because rights accumulate over time as teams rush to unblock delivery. Attackers target identity via phishing, token theft, OAuth abuse, and exploiting stale credentials. Compromising one over-privileged identity often unlocks lateral movement and data access. The solution is Zero Trust—assume breach, minimize privileges, verify continuously, and segment everything. A mature identity strategy aligns SSO/MFA with least privilege, short-lived credentials, and continuous evaluation of entitlements. With the right tools and processes, you shrink exposure without slowing developers. Over-privileged Identities and Key Sprawl “Just make it work” requests create policies with wildcard permissions. Months later, no one remembers why they exist. Meanwhile, API keys leak into repos, CI logs, or chat threads. Machine identities multiply for microservices, each needing lifecycle management. Address sprawl with Cloud Infrastructure Entitlement Management (CIEM) to visualize and right-size permissions. Rotate and vault secrets by default; prefer federation and short-lived tokens to long-lived keys. Tag identities with owners and expiry dates to make cleanup habitual rather than heroic. IAM Hardening Playbook (SSO, MFA, JIT, ABAC) Centralize identity with SSO and enforce MFA for all administrative roles. Use least privilege via role-based access control (RBAC), then evolve to attribute-based access control (ABAC) to handle scale and context. Adopt just-in-time (JIT) access: grant temporary elevated privileges with approvals and session recording. Prefer role assumption and workload identity federation over static keys; enforce automatic key rotation for any remaining secrets. These patterns align with Zero Trust principles and reduce both the likelihood and impact of compromised credentials. Challenge #3: Data Protection, Encryption, and Sovereignty Data is the target. Cloud simplifies storage and sharing, but without classification and controls you risk oversharing, shadow data,
How Does a VPN Affect Internet Speed? Facts and Fixes
How Does a VPN Affect Internet Speed? Facts and Fixes how does a vpn affect internet speed — this is one of the most common questions users ask when they consider installing a VPN. A VPN (Virtual Private Network) changes how your traffic travels on the internet: it encrypts data, routes it through a remote server, and can bypass ISP restrictions. Those processes can influence latency, throughput, and overall user experience, but the exact impact varies by protocol, server choice, network conditions, and device. This article explains the facts, shows how to measure the effects, and gives practical fixes to regain performance without compromising privacy. How VPNs Work: A Quick Technical Primer A VPN creates an encrypted "tunnel" between your device and a VPN server. All data you send and receive is encapsulated inside this tunnel and transported over the public internet. Because your traffic is encrypted and routed through another server, your apparent IP address changes and your data is protected from eavesdroppers such as public Wi‑Fi attackers and some ISPs. Encryption adds computational overhead. When data is encrypted and decrypted, your device and the VPN server need CPU cycles to perform cryptographic operations. This overhead can be minimal on modern hardware but becomes noticeable on older devices, routers without hardware acceleration, or when high-encryption ciphers are used. Stronger encryption increases privacy but can reduce raw throughput. Routing through a VPN server changes the network path. Instead of taking the direct route to a destination, packets travel to the VPN server first, which then forwards them to the target site or service. That detour increases round-trip time (RTT) and can add latency. The geographic distance, the VPN server’s load, and intermediate peering relationships all influence the magnitude of this effect. Encryption and overhead Encryption transforms readable data into ciphertext and requires resources for both encryption and decryption. On mobile devices and older laptops, CPU-bound encryption can reduce the maximum achievable download/upload speeds. VPN apps that support hardware-accelerated cryptography or lightweight protocols help reduce this cost. Different ciphers also vary in CPU intensity. For example, AES-NI accelerated AES ciphers are fast on modern CPUs, while some legacy ciphers are slower. Choosing a modern cipher and a protocol optimized for performance can significantly reduce the encryption overhead. Tunneling protocols VPN protocols (OpenVPN, WireGuard, IKEv2/IPsec, L2TP/IPsec, SSTP) define how tunnels are built and how encryption is handled. Protocols designed recently, like WireGuard, prioritize simplicity and speed; others like OpenVPN are feature-rich and very secure but can be slower due to design complexity and dependency on user-space processes. Protocol choice affects CPU usage, latency characteristics, and compatibility. For instance, WireGuard typically delivers higher throughput and lower latency compared to OpenVPN through UDP, while IKEv2 is known for fast reconnections and mobile stability. Protocol selection is one of the easiest levers to adjust if you want better speed. Server location and routing Where the VPN server is located relative to you and to your destination matters. A VPN server close to your physical location generally reduces additional latency; however, if that server then routes to a faraway destination poorly peered with the destination network, overall RTT increases. Similarly, a lightly loaded server will perform better than an overloaded one. Server selection is both geographic and performance-based. Primary Ways a VPN Impacts Internet Speed A VPN affects three core network metrics: latency (ping), bandwidth (download/upload throughput), and reliability (packet loss, jitter). Each metric influences different use cases — gaming cares about latency, streaming about consistent bandwidth, and video conferencing about both latency and jitter. Latency increases because traffic makes an extra hop to the VPN server. This is especially noticeable for interactive applications (online games, SSH, VoIP). For example, connecting to a VPN server on another continent adds the physical propagation delay of that distance plus queuing delays on intermediate routers. Bandwidth can drop because of encryption overhead, protocol inefficiencies, and server-side limits. Some VPN providers intentionally cap speeds on certain server plans. Additionally, ISPs sometimes throttle connections based on application-level patterns; a VPN can hide patterns but may still be subject to underlying network capacity and congestion. Reliability issues like packet loss and jitter arise when the VPN server or its network path is congested, poorly configured, or experiencing hardware problems. A VPN can both reduce packet loss (e.g., if the ISP route is problematic) or introduce it (if the VPN route is worse). Understanding which metric is suffering helps choose the right fix. Latency increase The additional physical and logical hops the VPN creates directly increase latency. If your VPN server is 2000 miles away, expect higher ping times than connecting to a local ISP gateway. Latency affects real-time interaction: a gamer or remote desktop user will notice lag immediately. Protocol overhead matters too: TCP-based VPNs with heavy reliability checks might add more latency compared to lightweight UDP-based tunnels. Choosing a nearby server and a low-latency protocol are primary tactics to reduce this impact. Bandwidth reduction Bandwidth drops manifest as slower downloads/uploads. Causes include encryption CPU limits, server throughput caps, or saturated peering links between the VPN server and destination. On a 100 Mbps ISP link, a badly configured VPN might only deliver 30–50 Mbps, while a well-optimized WireGuard setup could approach the ISP limit. Some VPN providers offer specialized high-speed servers for streaming or P2P that are provisioned with more bandwidth. Testing multiple servers and protocols often reveals which combination gets you closer to native speeds. Packet loss and jitter Packet loss occurs when routers drop packets because of congestion or errors; jitter is variation in packet arrival times. VPNs can sometimes stabilize an otherwise jittery route by forcing traffic through a better path, but they can also introduce jitter if the VPN server or its network is unstable. For real-time applications (VoIP/video calls), small packet loss and jitter spikes degrade call quality. Using VPNs with low server load and good peering reduces these problems; enabling QoS (Quality of Service) on local network equipment helps too. Measuring VPN Speed: Tools and
What Are the Principles of the CIA Triad in Security?
Title: What Are the Principles of the CIA Triad in Security? If you’re building or safeguarding digital systems, you’ve likely heard the term “CIA Triad.” But what exactly does it mean in practice, and why has it endured for decades? If you’re asking what are the principles of the cia triad in security, the short answer is: Confidentiality, Integrity, and Availability. The long answer—and the one that will truly help you design resilient, compliant, and business-aligned controls—requires understanding how these principles interlock, how threats exploit their gaps, and how to apply them across modern architectures like cloud, SaaS, APIs, and DevOps pipelines. This comprehensive guide breaks it all down with actionable insights, examples, and an evergreen roadmap you can adopt today. H2: Understanding the CIA Triad: Definition, Relevance, and OriginsThe CIA Triad is a foundational model in information security that guides how we protect data, systems, and services. Think of it as the de facto compass for aligning security work with business value: keeping secrets secret, ensuring correctness, and delivering reliability. Each pillar influences the others; a control that strengthens one may inadvertently weaken another if not properly designed. Despite its simplicity, the triad scales to complex ecosystems—multi-cloud deployments, remote workforces, and API-first applications—because it captures what stakeholders truly care about. Boards want to avoid fines and reputational damage (Confidentiality), analysts and data scientists need trusted data (Integrity), and customers expect uninterrupted service (Availability). The triad expresses these needs in security language. Critically, the CIA Triad continues to serve as a bridge between technical teams and leadership. Whether you’re pursuing ISO/IEC 27001 certification, aligning to the NIST Cybersecurity Framework, or preparing for SOC 2 audits, you will map your controls and evidence back to confidentiality, integrity, and availability. It’s not only the “why” of security—it’s the “how.” H3: 1. Definition and ComponentsThe triad’s three principles are: Confidentiality: Ensuring information is accessible only to those authorized to view it. Integrity: Ensuring information is accurate, consistent, and unaltered except by authorized actors. Availability: Ensuring systems and data are accessible and usable when required. These principles are agnostic to technology. Whether you’re storing customer records in a relational database, streaming telemetry in a data lake, or serving content from an edge network, the same three outcomes define successful protection. That makes the triad an evergreen mental model—even as tech stacks evolve. Each principle also has a risk lens. Confidentiality addresses data leaks and unauthorized access. Integrity addresses tampering, errors, and unsanctioned changes. Availability addresses downtime and performance degradation. In practice, your program must balance all three based on business priorities and risk appetite. H3: 2. Historical Origins and EvolutionThe CIA Triad emerged from early information assurance and computer security research in the late 20th century, where military and academic disciplines intersected. Over time, as businesses digitized, the triad transcended its origins. It became the lingua franca across industries—from healthcare to finance—because the trio maps equally well to medical records, trading systems, and SaaS platforms. As threats evolved from lone actors to organized cybercrime and nation-state operations, the triad remained intact but gained new implementation patterns. Encryption moved from niche to ubiquitous, hash-based integrity checks became pervasive, and high availability matured into multi-region, multi-cloud strategies. The model stayed constant while the controls advanced. Today, the triad integrates with wider frameworks: Zero Trust architectures emphasize strict access control (C), strong device and workload identities (I), and microsegmented, resilient services (A). DevSecOps pipelines embed integrity checks (I), secrets management (C), and automated rollbacks and redundancy (A). Same compass, modern map. H3: 3. Why the CIA Triad Still MattersThe triad persists because it’s practical, measurable, and communicable. Executives can understand and fund it; engineers can implement and test it; auditors can verify it. That’s rare alignment. Its simplicity also helps avoid tunnel vision: when racing to encrypt everything, teams remember to check integrity and availability implications, keeping security from becoming a single-issue program. Moreover, the triad’s focus on outcomes helps you cut through buzzwords. Whether your vendor touts AI-powered detection or post-quantum crypto, you can ask: Does this improve confidentiality, integrity, availability—or is it just noise? That clarity keeps budgets focused and architectures sane. Finally, the triad is future-proof. As cryptographic standards evolve, edge computing expands, and regulations tighten, the same three aims remain your anchor. You can modernize tools without losing sight of goals. H2: Principle 1: Confidentiality — Keeping Data SecretConfidentiality protects data from unauthorized access and disclosure. It applies to data at rest, in transit, and in use. Strong confidentiality reduces legal exposure, preserves trust, and prevents extortion scenarios like ransomware leaks. It’s also essential for compliance regimes such as GDPR, HIPAA, PCI DSS, and many regional privacy laws. The biggest misconception is that encryption alone guarantees confidentiality. It doesn’t. You also need identity and access management, key management, least privilege, and secure coding patterns to prevent logic flaws that expose data. Equally important is operational discipline: secrets rotation, audit logging, and tailored monitoring. Done right, confidentiality safeguards both structured and unstructured content—databases, object storage, logs, backups, and even model weights in ML systems. The control set is broad because data sprawls across environments. H3: 1. Core Controls for ConfidentialityConfidentiality stems from layered defenses: Strong authentication (MFA, phishing-resistant methods like FIDO2) to reduce account takeover. Fine-grained authorization via RBAC/ABAC and the principle of least privilege. Encryption at rest (AES-256 or equivalent) with centralized, rotated keys; HSM-backed key custodianship. Encryption in transit (TLS 1.2+), certificate pinning where feasible, and secure cipher suites. Data classification and labeling to drive policy: public, internal, confidential, restricted. Data Loss Prevention (DLP) for egress control, plus CASB for SaaS visibility. Secrets management for API keys, tokens, and credentials—never hard-code secrets. Privacy by design: minimize data collection, tokenize or pseudonymize when possible. Controls should be automated to avoid drift. For example, enforce encryption-by-default policies and guardrails in cloud templates. Automation ensures consistency at scale across new and existing assets. Key management deserves special care. Separate duties for key creation, rotation, and usage; log every access; and deploy envelope encryption to
Does a VPN Protect From Viruses? What You Need to Know
Does a VPN Protect From Viruses? What You Need to Know If you’ve ever asked yourself, “does a vpn protect from viruses,” you’re not alone. It’s a common—and important—question in a world where we spend much of our lives online. The short answer: a VPN is not antivirus software, but it can reduce certain risks that lead to infections. To stay truly safe, you need to understand what a VPN actually does, where it helps, and where it doesn’t—and how to build a layered defense that includes more than one tool. What a VPN Really Does (and What It Doesn’t) At its core, a Virtual Private Network (VPN) encrypts your internet traffic and routes it through a secure server. This makes your data unreadable to snoops on the same network and hides your IP address from websites, advertisers, and many types of trackers. On untrusted Wi‑Fi, that encryption is a powerful shield against passive eavesdropping and some forms of active tampering. However, a VPN is not a malware scanner. It doesn’t inspect the files you download, analyze email attachments, or quarantine suspicious apps. If you click a malicious link and download ransomware, the VPN won’t stop that executable from running on your device. Think of a VPN as a privacy and network security tool—not an endpoint antivirus or EDR (endpoint detection and response) solution. That said, VPNs can indirectly prevent infections by blocking some paths attackers use. For example, some VPNs offer DNS filtering that stops connections to known malicious domains. Others include tracker blocking or “Threat Protection” add-ons. These features help reduce risk, but they’re not a substitute for real-time malware protection on your device. What a VPN does well: Encrypts internet traffic on risky networks Masks your IP address and location Helps prevent ISP/ad-injection and some MITM attacks What a VPN does not do: Scan files for viruses Remove malware already on your device Replace antivirus, EDR, or patching How Viruses and Malware Actually Infect Devices Understanding the modus operandi of malware helps clarify where a VPN fits. Most infections happen through human interaction—phishing emails, fake software updates, or malicious downloads—rather than magical “over-the-air” compromise. Phishing remains the top entry point. Attackers craft convincing emails or messages that lure you into clicking links or opening attachments. Once you enable macros or run an installer, the malware executes. The presence of a VPN doesn’t change that basic sequence of events. Exploits are another vector. Unpatched browsers, VPN clients, browser extensions, or document readers can be targeted through drive-by downloads on compromised sites. Here, a VPN won’t stop the exploit itself, but a VPN with DNS or URL filtering might block the known-bad domain before the page loads. Common infection vectors include: Phishing attachments and links Malicious advertisements (malvertising) Trojans disguised as free software or “cracks” Exploits against outdated software Infected USB devices or local network shares When a VPN Can Help — Indirect Protections That Matter Even though a VPN doesn’t disinfect your device, it can reduce exposure to risk. On public Wi‑Fi—airports, cafés, hotels—unencrypted traffic is low-hanging fruit for attackers. A VPN encrypts your session end-to-end, thwarting many snooping attempts and some forms of content injection that could otherwise deliver malware. Some VPN services add DNS filtering to block malicious or typosquatted domains, cutting off access to known phishing kits and command-and-control servers. While this won’t catch everything, it can stop you from landing on a dangerous page in the first place—a meaningful risk reduction in the kill chain. Additionally, masking your IP with a VPN can deter opportunistic scanning and certain IP-based attacks. Attackers who rely on IP reputation or geofenced campaigns may find you a harder target. It’s not invisibility, but it’s another layer that increases their cost and decreases your exposure. 1. Public Wi‑Fi: A Realistic Use Case Where VPNs Shine On open networks, attackers can sniff traffic, perform SSL stripping in poorly configured scenarios, or inject malicious scripts if a site lacks proper HTTPS. A reputable VPN ensures your traffic stays encrypted from your device to the VPN server, preventing in situ interception or tampering. Even in environments with captive portals or shared passwords, your VPN tunnel isolates you from other users. This reduces risk from rogue APs and evil-twin hotspots attempting to capture credentials or inject malware through content manipulation. 2. Stopping Some Bad Domains Before You Reach Them If your VPN includes DNS filtering or “safe browsing” features, it can block your device from resolving known-malicious domains. This is particularly effective against phishing links and malware distribution networks that rely on fast-changing infrastructure. While DNS filtering isn’t perfect—it can be bypassed by direct IP connections or brand-new domains—it adds friction for attackers and reduces your exposure to common threats. It also helps prevent callbacks to command-and-control servers, potentially neutering certain malware even if it executes. What a VPN Won’t Do Against Viruses (and What Will) It’s critical to be precise: a VPN doesn’t scan files, detect ransomware, or clean infections. If you download a malicious PDF and your reader is vulnerable, the VPN won’t rescue you. If you run a trojanized installer, your VPN has no power to stop the binary from encrypting your files. What will help? Real-time endpoint protection, frequent patching, and safe browsing habits. Next-gen antivirus/EDR tools monitor process behavior and can block known and unknown threats. OS and app updates seal off known vulnerabilities. Browser hardening and email security reduce the chance of encountering malware in the first place. To visualize where each tool fits, consider this quick comparison: Layer/Capability VPN Antivirus/EDR Firewall DNS Filter Auto-Update/Patching Encrypts traffic on public Wi‑Fi Yes No No No No Hides IP address Yes No No No No Blocks malware downloads Partial (if feature exists) Yes No Partial No Detects/removes viruses No Yes No No No Blocks malicious domains Partial (if feature exists) Partial (web shield) No Yes No Stops exploits No Partial (behavior shields) No No Partial (by patching) Prevents lateral network attacks Partial (isolation) Partial Yes (segmentation) No No
Best VPN for Firestick in 2025 – Fast & Secure Streaming
Discover the best VPN for Firestick in 2025 for fast, secure streamingexplore top picks like ExpressVPN and Surfshark tailored for US users.